AWS CloudTrail Integration Prerequisites
This topic explains how to prepare for Lacework CloudTrail integration using manual configuration.
If you plan to use Terraform, see AWS Terraform.
If you plan to use CloudFormation, see AWS Integration Using CloudFormation.
Prerequisites
- SNS topic - An Amazon Simple Notification Service (SNS) topic is a logical access point that acts as a communication channel. A topic lets you group multiple endpoints, such as AWS, Amazon SQS, HTTP/S, or an email address. All CloudTrail integrations require an SNS topic. Lacework can use an existing SNS topic or create one if you have not added an SNS topic to an existing CloudTrail.
- SQS queue - Amazon Simple Queue Service (SQS) is a message queue service used by distributed applications to exchange messages through a polling model. SQS decouples sending and receiving components without requiring each component to be concurrently available. Used together, Amazon SNS and Amazon SQS can deliver messages to applications that require immediate notification of an event. Messages are also persisted in an Amazon SQS queue for other applications to process at a later time. All CloudTrail integrations require an SQS queue.
- S3 bucket - A bucket is a container for objects stored in Amazon S3. All CloudTrail integrations require an S3 bucket. Lacework can use an existing bucket or create one in the designated account.
- CloudTrail - AWS CloudTrail is an AWS service that helps you enable governance, compliance, and operational and risk auditing of your AWS account. Actions taken by a user, role, or an AWS service are recorded as events in CloudTrail. Lacework can use an existing CloudTrail or create a new trail.
- Cross-account IAM role - The cross-account role provides Lacework the access to analyze CloudTrail events. Create the cross-account role for Lacework to use.
- Custom IAM policy - The custom policy defines additional services that Lacework needs. Create the policy and grant it to the cross-account role.
Ensure that your cross-account IAM role and S3 bucket are collocated in the same AWS account - whether you're trying to configure this manually, via CloudFormation, or Terraform. This is related to legacy AWS rules that govern access to objects created inside S3 buckets that are beyond Lacework’s control. Setting up cross-account access is not enough to work around this issue.
Additional Requirements
- AWS account admin - The account must have administrative privileges for every AWS account that you want to integrate with Lacework.
- Lacework administrator - You must have a Lacework account with administrator privileges.
- Ensure that you are deploying the integration to a supported AWS region.
Pipeline Options
Lacework supports three pipelines to integrate with AWS:
The pipeline design depends on your current environment and your future design goals. Consider the following points:
- As long as the data arrives at Lacework, your pipeline design choices are up to you.
- For example, if your SNS topic is in a separate AWS account, you can choose not to use SNS.
- Also, if your existing S3 bucket is already sending messages to your existing SQS queue, setting up a new S3 to SQS notification for Lacework is not possible because both notifications require the same suffix (not allowed by AWS). In this case, you can move to an SNS fanout.
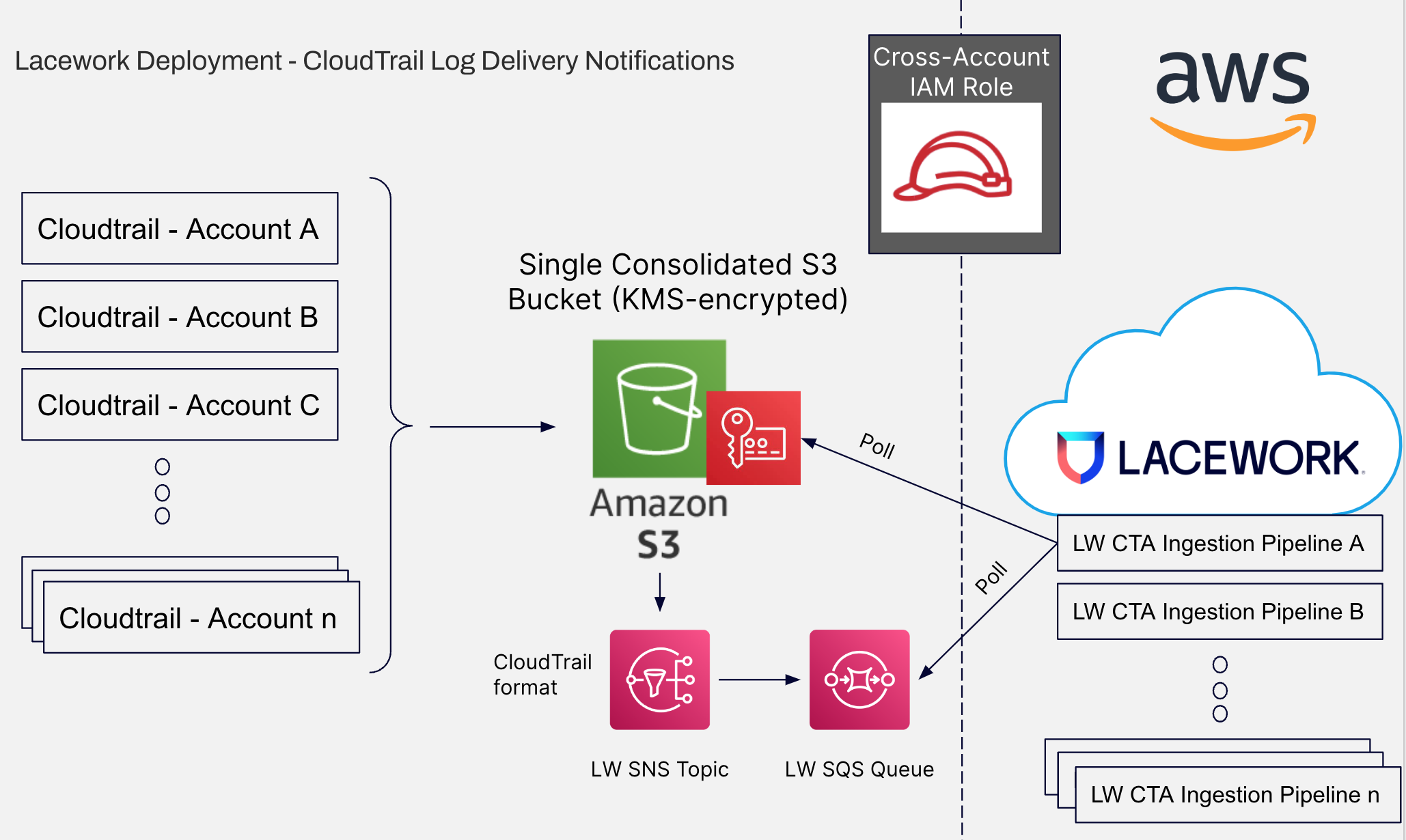
CloudTrail Log Delivery Notifications
The following diagram shows a simple presentation of the AWS integration using CloudTrail SNS notifications.
Create an SNS Topic
An SNS topic is a communication channel for SQS queue messaging from your AWS environment to Lacework.
If you already have an SNS topic for integration, record the ARN for the topic. If you do not have an SNS topic, use the following steps to create one.
- Log in to your AWS account.
- Go to the Amazon Simple Notification Service page.
- Click Topics.
- Click Create topic.
- Select the Standard type of topic.
- Enter a name and display name for the new topic.
- Click Create topic. Details of the new SNS topics appear along with the ARN for the topic.
- Record the ARN for the new topic. You will need this information when you configure integration from the Lacework Console.
Configure the Access Policy for Your SNS Topic
Select the Access policy tab for your SNS topic.
Click the Edit option.
Copy the following JSON file and replace the existing policy (using the ARN you just recorded):
Expand to view the JSON file
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "AWSCloudTrailSNSPolicy",
"Effect": "Allow",
"Principal": {
"Service": "cloudtrail.amazonaws.com"
},
"Action": "SNS:Publish",
"Resource": "<ARN_of_SNS_Topic>"
}
]
}Click Save.
By default, the topic owner has permissions to publish the topic. To enable other users or applications to publish to the topic, use AWS Identity and Access Management (IAM) to give publish permission to the topic. For more information about giving permissions for Amazon SNS actions to IAM users, see Using identity-based policies with Amazon SNS.
Set Up CloudTrail SNS Delivery
Create an S3 Bucket
S3 buckets store CloudTrail log files and are containers for objects stored in Amazon S3. Ensure that you have an AWS S3 bucket available to store CloudTrail log files.
- Log in to your AWS account.
- Go to the Amazon S3 page.
- Click Create bucket to create a new S3 bucket. The Create bucket page appears.
- Enter a name for your new S3 bucket in Bucket name.
- Select an AWS region for your S3 bucket from the dropdown.
- Select all other default settings or specify your requirements.
- Click Create bucket.
Create a CloudTrail for Monitoring Your AWS Environment
Ensure that you have a CloudTrail available for monitoring AWS activity for your account. CloudTrail stores multiple events in a log file. This log file is delivered to the specified AWS S3 bucket. Lacework uses CloudTrail log files for monitoring your AWS cloud environment.
- Log in to your AWS account.
- Go to the CloudTrail dashboard.
- Click Create trail.
- In the Trail name field, enter a name for your new CloudTrail.
- Select Use existing S3 bucket.
- Click Browse to select the S3 bucket to store CloudTrail log files from the dropdown list.
- In the Event type section, select Management events.
Lacework ingests management events only, see Log Types for more information. - Select the types of management event API activity you want to log in your CloudTrail: Read, Write, Exclude AWS KMS events and/or Exclude Amazon RDS Data API events.
- Click Next to proceed with your CloudTrail creation.
- Review your CloudTrail configuration.
- Click Create trail.
Enable SNS Notification Delivery for CloudTrail
You can enable SNS notification delivery for any CloudTrail writing data to your central AWS S3 bucket. A notification is sent to the SNS topic for every log file delivered to your S3 bucket.
- Log in to your AWS account.
- Go to the CloudTrail dashboard. A list of CloudTrails appears in your account.
- Select a CloudTrail to monitor and enable SNS notification.
- Click Edit.
- Select Enabled for the SNS notification delivery option.
- Select Existing for the Create a new SNS topic to use the SNS topic created in a previous task.
- Select the new SNS topic created earlier from the dropdown list, or enter the ARN for the new SNS topic.
- Click Save changes.
Set Up the SQS Queue
Amazon Simple Queue Service (SQS) is a message queue service used by distributed applications to exchange messages through a polling model. SQS decouples sending and receiving components without requiring each component to be concurrently available. Used together, Amazon SNS and Amazon SQS can deliver messages to applications that require immediate notification of an event. Messages are also persisted in an Amazon SQS queue for other applications to process at a later time. All CloudTrail integrations require an SQS queue.
Create an SQS Queue
Ensure that you have an SQS queue available to integrate with Lacework.
- Log in to your AWS account.
- Go to the Amazon Simple Queue Service page.
- Click Create queue to create a new SQS queue.
- Select the Standard type of queue.
- Enter a name for the new queue.
- Accept the default values for your queue or configure for your specific requirements if necessary.
- Click Create queue. Details of the new SQS queue appear along with the ARN and URL for the topic.
- Record the ARN and URL for the new queue. You will need the ARN for the next step, and you will need the URL when you configure integration from the Lacework Console.
Configure the Access Policy for Your SQS Queue
Select the Access policy tab for your SQS queue.
Click the Edit option.
Copy the following JSON file and replace the existing policy (using the ARN you just recorded):
Expand to view the JSON file
{
"Version": "2012-10-17",
"Id": "lacework_sqs_policy",
"Statement": [
{
"Sid": "AllowLaceworkSNSTopicToSendMessage",
"Effect": "Allow",
"Principal": {
"AWS": "*"
},
"Action": "SQS:SendMessage",
"Resource": "<ARN_of_SQS_Queue>",
"Condition": {
"ArnEquals": {
"aws:SourceArn": "<ARN_of_SNS_Topic>"
}
}
}
]
}Click Save.
Subscribe Your SQS Queue to Your SNS Topic
- Select the SNS Subscription tab for your SQS queue.
- Click the Subscribe to Amazon SNS topic option.
- Select the SNS topic you created in the previous task from the dropdown list, or paste the SNS topic ARN.
- Click Save.
Create an IAM Policy and Role
To allow Lacework access to the required resources on your AWS environment, you must create the following:
- A custom IAM policy
- A cross-account IAM role
Create a Custom IAM Policy
Create a custom policy that gives Lacework read-only access to ingest CloudTrail logs.
Log in to your AWS account.
Go to the Identity and Access Management (IAM) dashboard.
Click Policies in the left sidebar. A list of existing IAM policies appears.
Click Create Policy.
Select JSON and paste the following JSON file into the text box to define your new IAM policy for CloudTrail. Add the missing ARNs before you go to the next step.
To define a combined IAM policy for a CloudTrail+Configuration integration, use the following policy. Add the missing ARNs before you go to the next step. Ensure you also grant the AWS managed SecurityAudit IAM policy to the cross-account IAM role you create in the next section.Expand to view the JSON file
{
"Statement": [
{
"Action": "s3:Get*",
"Effect": "Allow",
"Resource": "<ARN_for_S3_bucket>/*",
"Sid": "ReadLogFiles"
},
{
"Action": "iam:ListAccountAliases",
"Effect": "Allow",
"Resource": "*",
"Sid": "GetAccountAlias"
},
{
"Action": "s3:ListBucket",
"Condition": {
"StringLike": {
"s3:prefix": "*AWSLogs/"
}
},
"Effect": "Allow",
"Resource": "<ARN_for_S3_bucket>",
"Sid": "ListLogFiles"
},
{
"Action": [
"sqs:ReceiveMessage",
"sqs:GetQueueUrl",
"sqs:GetQueueAttributes",
"sqs:DeleteMessage"
],
"Effect": "Allow",
"Resource": "<ARN_for_SQS_Queue>",
"Sid": "ConsumeNotifications"
},
{
"Action": [
"sns:ListTopics",
"sns:ListSubscriptionsByTopic",
"sns:ListSubscriptions",
"sns:GetTopicAttributes",
"sns:GetSubscriptionAttributes",
"s3:ListAllMyBuckets",
"s3:GetBucketPolicy",
"s3:GetBucketLogging",
"s3:GetBucketLocation",
"s3:GetBucketAcl",
"cloudtrail:ListPublicKeys",
"cloudtrail:GetTrailStatus",
"cloudtrail:GetTrail",
"cloudtrail:DescribeTrails"
],
"Effect": "Allow",
"Resource": "*",
"Sid": "Debug"
}
],
"Version": "2012-10-17"
}Expand to view the JSON file
{
"Statement": [
{
"Action": "s3:Get*",
"Effect": "Allow",
"Resource": "<ARN_for_S3_bucket>/*",
"Sid": "ReadLogFiles"
},
{
"Action": "iam:ListAccountAliases",
"Effect": "Allow",
"Resource": "*",
"Sid": "GetAccountAlias"
},
{
"Action": "s3:ListBucket",
"Condition": {
"StringLike": {
"s3:prefix": "*AWSLogs/"
}
},
"Effect": "Allow",
"Resource": "<ARN_for_S3_bucket>",
"Sid": "ListLogFiles"
},
{
"Action": [
"sqs:ReceiveMessage",
"sqs:GetQueueUrl",
"sqs:GetQueueAttributes",
"sqs:DeleteMessage"
],
"Effect": "Allow",
"Resource": "<ARN_for_SQS_Queue>",
"Sid": "ConsumeNotifications"
},
{
"Action": [
"sns:ListTopics",
"sns:ListSubscriptionsByTopic",
"sns:ListSubscriptions",
"sns:GetTopicAttributes",
"sns:GetSubscriptionAttributes",
"s3:ListAllMyBuckets",
"s3:GetBucketPolicy",
"s3:GetBucketLogging",
"s3:GetBucketLocation",
"s3:GetBucketAcl",
"cloudtrail:ListPublicKeys",
"cloudtrail:GetTrailStatus",
"cloudtrail:GetTrail",
"cloudtrail:DescribeTrails"
],
"Effect": "Allow",
"Resource": "*",
"Sid": "Debug"
},
{
"Action": "ec2:GetEbsEncryptionByDefault",
"Effect": "Allow",
"Resource": "*",
"Sid": "GetEc2DefaultEncryption"
},
{
"Action": "eks:ListTagsForResource",
"Effect": "Allow",
"Resource": "*",
"Sid": "EksListTagsForResource"
},
{
"Action": [
"elasticfilesystem:DescribeReplicationConfigurations",
"elasticfilesystem:DescribeLifecycleConfiguration",
"elasticfilesystem:DescribeFileSystemPolicy",
"elasticfilesystem:DescribeBackupPolicy",
"elasticfilesystem:DescribeAccountPreferences",
"elasticfilesystem:DescribeAccessPoints"
],
"Effect": "Allow",
"Resource": "*",
"Sid": "EfsPolicies"
},
{
"Action": [
"sagemaker:GetModelPackageGroupPolicy",
"sagemaker:GetLineageGroupPolicy"
],
"Effect": "Allow",
"Resource": "*",
"Sid": "SagemakerPolicies"
},
{
"Action": [
"identitystore:ListUsers",
"identitystore:ListGroups",
"identitystore:ListGroupMembershipsForMember",
"identitystore:ListGroupMemberships",
"identitystore:DescribeUser",
"identitystore:DescribeGroupMembership",
"identitystore:DescribeGroup"
],
"Effect": "Allow",
"Resource": "*",
"Sid": "IdentityStoreReadOnly"
},
{
"Action": [
"sso:GetInlinePolicyForPermissionSet",
"sso:DescribeInstanceAccessControlAttributeConfiguration",
"sso:DescribeAccountAssignmentDeletionStatus"
],
"Effect": "Allow",
"Resource": "*",
"Sid": "SSOReadOnly"
},
{
"Action": "apigateway:GET",
"Effect": "Allow",
"Resource": [
"arn:aws:apigateway:*::/apikeys",
"arn:aws:apigateway:*::/apikeys/*"
],
"Sid": "APIGATEWAY"
},
{
"Action": [
"glue:ListWorkflows",
"glue:BatchGetWorkflows",
"glue:GetTags"
],
"Effect": "Allow",
"Resource": "*",
"Sid": "GLUE"
},
{
"Action": [
"waf-regional:ListRules",
"waf-regional:GetRule",
"waf-regional:ListRuleGroups",
"waf-regional:GetRuleGroup",
"waf-regional:ListActivatedRulesInRuleGroup"
],
"Effect": "Allow",
"Resource": "*",
"Sid": "WAFREGIONAL"
},
{
"Action": [
"codebuild:ListBuilds",
"codebuild:BatchGetBuilds"
],
"Effect": "Allow",
"Resource": "*",
"Sid": "CODEBUILD"
}
],
"Version": "2012-10-17"
}Click Next.
Specify a policy name in Name and a brief description of your policy.
Optionally add tags as key-value pairs to AWS resources to identify them.
Click Create policy. Your new IAM policy appears in the list of policies for your AWS environment.
Create a Cross-Account IAM Role
Lacework requires a cross-account role to analyze CloudTrail events. The cross-account IAM role must be located within the same account as the S3 bucket.
- Log in to your AWS account.
- Go to the Identity and Access Management (IAM) dashboard.
- Click Roles in the left sidebar. A list of existing IAM roles appears.
- Click Create role.
- For Trusted entity type, select Custom trust policy.
- Add the following policy statement:
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "Statement",
"Effect": "Allow",
"Principal": {
"AWS": "arn:aws:iam::434813966438:role/lacework-platform"
},
"Action": "sts:AssumeRole",
"Condition": {
"StringEquals": {
"sts:ExternalId": [
"lweid:aws:v2:<tenant_name>:<aws_account_id>:<unique_id>"
]
}
}
}
]
}434813966438:role/lacework-platformis the Lacework account ID and Lacework role name.- For
sts:ExternalId, provide an external ID, which must consist of your Lacework tenant name (from your Lacework URL<tenant_name>.lacework.net), AWS account being integrated, and a random 10 character string. See the complete external ID format details to verify it is Lacework-compliant. Copy the external ID so you can use it later in the onboarding process when you configure the integration from the Lacework Console.
- Click Next. The Add permissions page appears.
- Add the custom CloudTrail IAM policy you created earlier. If you are also creating a Config integration, add the AWS managed SecurityAudit policy.
- Click Next.
- Name the new role.
- Click Create role.
- Record the ARN for this cross-account role. You will need this information when you configure integration from the Lacework Console.
- Proceed to AWS Integration - Manual Configuration and follow the steps to complete the integration from the Lacework Console.
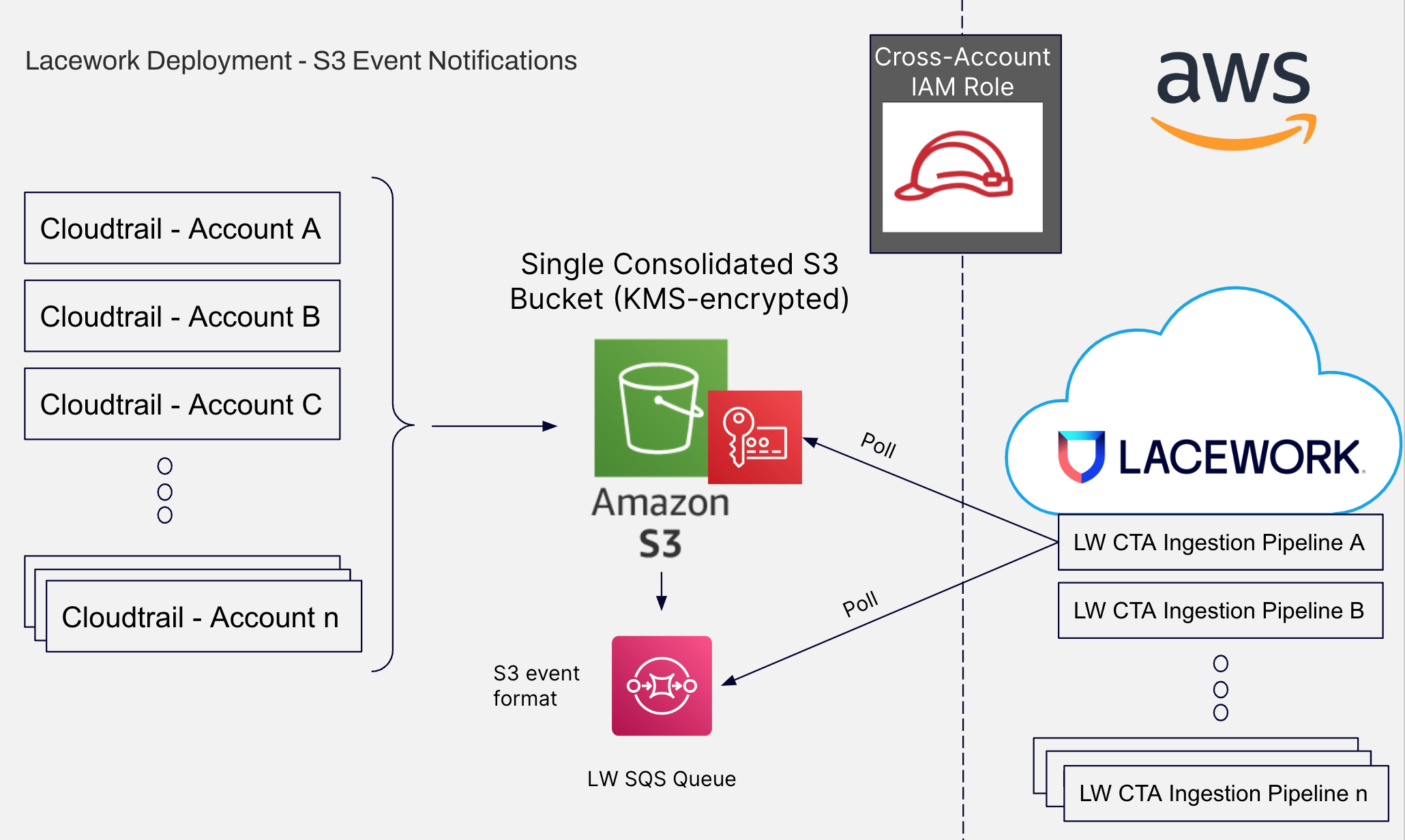
S3 Event Notifications
The following diagram shows a simple presentation of the AWS integration using S3 event notifications.
Set Up the SQS Queue to Receive Notifications from the S3 Bucket
To grant Amazon S3 permissions to publish messages to the SQS queue, attach an AWS Identity and Access Management (IAM) policy to the destination SQS queue. See IAM policy for a destination SQS queue.
Enable and Configure the S3 Bucket to Send Notifications to the SQS Queue
You can enable certain Amazon S3 bucket events to send a notification message to a destination whenever those events occur.
Sign in to the AWS Management Console and open the Amazon S3 console.
In the Buckets list, choose the name of the bucket that you want to enable events for.
Choose Properties.
Go to the Event Notifications section and choose Create event notification.
In the General configuration section, specify a descriptive event name for your event notification. Optionally specify a prefix and a suffix to limit the notifications to objects with keys ending in the specified characters.
a. Enter a description for the Event name. If you don't enter a name, a globally unique identifier (GUID) is generated and used for the name.
b. (Optional) To filter event notifications by prefix, enter a Prefix.
For example, you can set up a prefix filter so that you receive notifications only when files are added to a specific folder (for example,AWSLogs/).
c. (Optional) To filter event notifications by suffix, enter a Suffix.In the Event types section, select s3:ObjectCreated:*.
In the Destination section, choose the event notification destination.
a. Select the destination type as SQS Queue.
b. After you choose your destination type, choose a queue from the list.
c. Or, if you prefer to specify an ARN, select Enter SQS queue ARN and enter the ARN.Choose Save changes, and Amazon S3 sends a test message to the event notification destination.
Create an IAM Policy and Role
To allow Lacework access to the required resources on your AWS environment, you must create the following:
- CloudTrail custom IAM policy
- Cross-account IAM role
Create a CloudTrail Custom IAM Policy
Create a custom policy that gives Lacework read-only access to ingest CloudTrail logs:
Log in to your AWS account.
Go to the Identity and Access Management (IAM) dashboard.
Click Policies in the left sidebar. A list of existing IAM policies appears.
Click Create Policy.
Select the JSON tab and paste the following JSON file into the text box to define your new IAM policy for CloudTrail. Add the missing ARNs before you go to the next step.
Expand to view the JSON file
{
"Statement": [
{
"Action": "s3:Get*",
"Effect": "Allow",
"Resource": "<ARN_for_S3_bucket>/*",
"Sid": "ReadLogFiles"
},
{
"Action": "iam:ListAccountAliases",
"Effect": "Allow",
"Resource": "*",
"Sid": "GetAccountAlias"
},
{
"Action": "s3:ListBucket",
"Condition": {
"StringLike": {
"s3:prefix": "*AWSLogs/"
}
},
"Effect": "Allow",
"Resource": "<ARN_for_S3_bucket>",
"Sid": "ListLogFiles"
},
{
"Action": [
"sqs:ReceiveMessage",
"sqs:GetQueueUrl",
"sqs:GetQueueAttributes",
"sqs:DeleteMessage"
],
"Effect": "Allow",
"Resource": "<ARN_for_SQS_Queue>",
"Sid": "ConsumeNotifications"
},
{
"Action": [
"s3:ListAllMyBuckets",
"s3:GetBucketPolicy",
"s3:GetBucketLogging",
"s3:GetBucketLocation",
"s3:GetBucketAcl",
"cloudtrail:ListPublicKeys",
"cloudtrail:GetTrailStatus",
"cloudtrail:GetTrail",
"cloudtrail:DescribeTrails"
],
"Effect": "Allow",
"Resource": "*",
"Sid": "Debug"
}
],
"Version": "2012-10-17"
}Click Next: Tags to proceed with your policy creation.
Optionally add tags as key-value pairs to AWS resources to identify them.
Click Next: Review to proceed with your policy creation.
Specify a policy name in Name and a brief description of your policy.
Click Create policy. Your new IAM policy appears in the list of policies for your AWS environment.
Create a Cross-Account IAM Role
To create a cross-account IAM role, see Create a Cross-Account IAM Role.
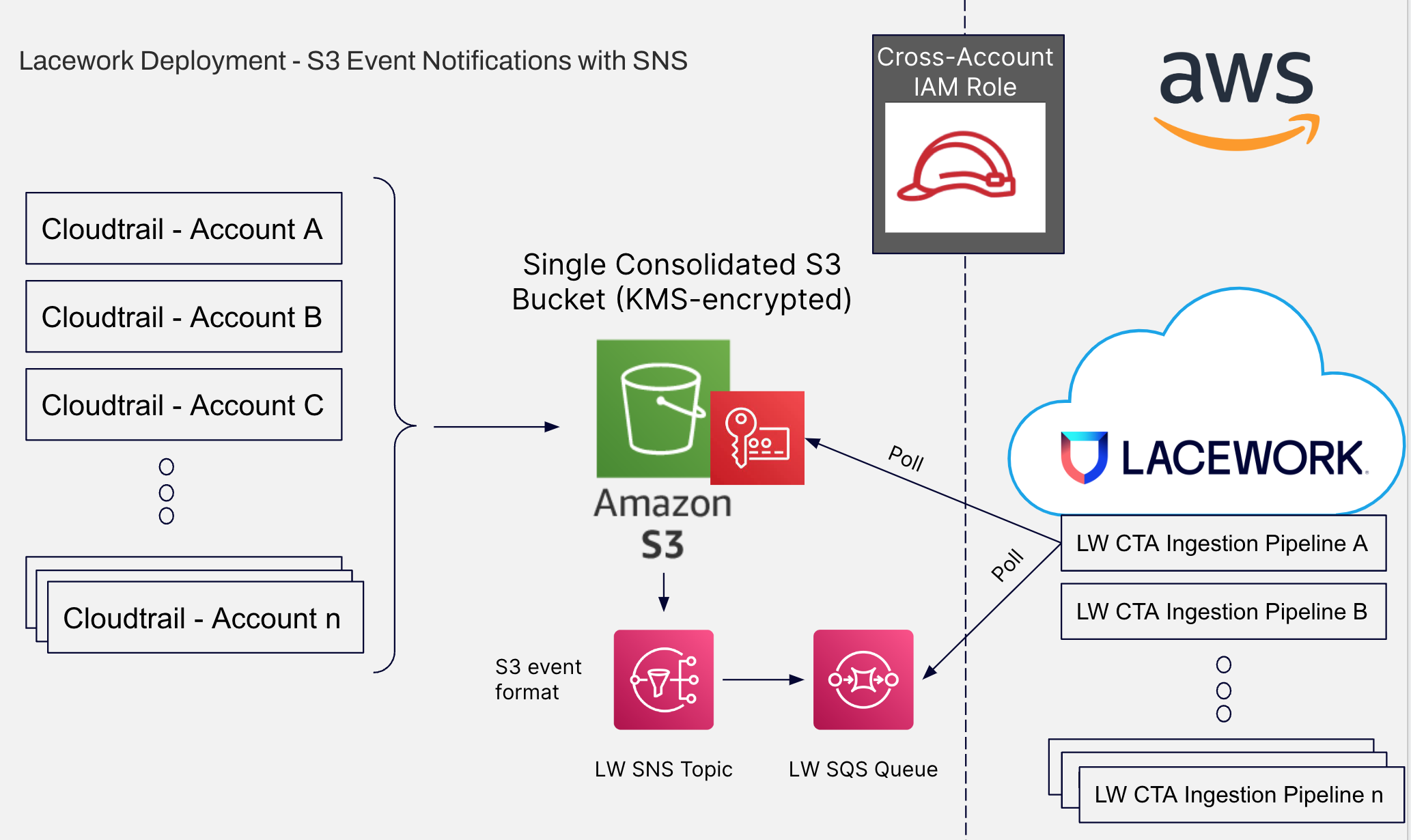
S3 Event Notifications with SNS
The following diagram shows a simple presentation of the AWS integration with S3 event notifications and SNS.
Create an SNS Topic
If you already have an SNS topic for integration, record the ARN for the topic. If you do not have an SNS topic, follow the steps in Create an SNS Topic to create one.
Set Up the SQS Queue
To create an SQS queue, see Set Up the SQS Queue.
Set Up the SNS Topic to Receive Notifications from the S3 Bucket
You must grant the Amazon S3 principal the necessary permissions to call the relevant API to publish messages to an SNS topic. This lets Amazon S3 publish event notification messages to a destination.
The following is an example of an AWS Identity and Access Management (IAM) policy that you attach to the destination SNS topic.
Expand to view the example policy
{
"Version": "2012-10-17",
"Id": "example-ID",
"Statement": [
{
"Sid": "Example SNS topic policy",
"Effect": "Allow",
"Principal": {
"Service": "s3.amazonaws.com"
},
"Action": [
"SNS:Publish"
],
"Resource": "SNS-topic-ARN",
"Condition": {
"ArnLike": {
"aws:SourceArn": "arn:aws:s3:*:*:bucket-name"
},
"StringEquals": {
"aws:SourceAccount": "bucket-owner-account-id"
}
}
}
]
}
For more information, see Granting permissions to publish event notification messages to a destination.
Enable and Configure Event Notifications Using the Amazon S3 Console
You can enable certain Amazon S3 bucket events to send a notification message to a destination whenever those events occur.
Sign in to the AWS Management Console and open the Amazon S3 console.
In the Buckets list, choose the name of the bucket that you want to enable events for.
Choose Properties.
Go to the Event Notifications section and choose Create event notification.
In the General configuration section, specify a descriptive event name for your event notification. Optionally specify a prefix and a suffix to limit the notifications to objects with keys ending in the specified characters.
a. Enter a description for the Event name. If you don't enter a name, a globally unique identifier (GUID) is generated and used for the name.
b. (Optional) To filter event notifications by prefix, enter a Prefix.
For example, you can set up a prefix filter so that you receive notifications only when files are added to a specific folder (for example,AWSLogs/).
c. (Optional) To filter event notifications by suffix, enter a Suffix.In the Event types section, select s3:ObjectCreated:*.
In the Destination section, choose the event notification destination.
a. Select the destination type as SNS Topic.
b. After you choose your destination type, choose a topic from the list.
c. Or, if you prefer to specify an ARN, select Enter SNS topic ARN and enter the ARN.Choose Save changes, and Amazon S3 sends a test message to the event notification destination.
Subscribe the SQS Queue to the SNS Topic
You can subscribe one or more SQS queues to an SNS topic. When you publish a message to a topic, the SNS sends the message to each of the subscribed queues. Amazon SQS manages the subscription and any necessary permissions. See Subscribing an Amazon SQS queue to an Amazon SNS topic (console).
Create an IAM Policy and Role
To create an IAM policy and role, refer to Create an IAM Policy and Role.