Azure Activity Log Integration - Manual Configuration
To create a Lacework Azure Activity Log integration to gather, process, report, and alert on an Azure subscription's activity, follow the procedures below. For Azure configuration and posture compliance, you must create a separate Azure compliance integration. For more information, see Integrate Lacework with Azure.
You do not need to create an Azure Compliance integration to create an Azure Activity Log integration. You can, however, use the same credentials for both integrations, even if they require different levels of permissions.
When an Azure Activity Log integration is created, Lacework gathers the logs of administrative operations at an Azure subscription level (see Microsoft's description of their log types). Lacework uses Azure Monitor's Diagnostic Settings, which exports the same type of logs in a folder named "insights-activity-logs". Inside is a folder structure that includes the Subscription ID which allows Lacework to consolidate logs from multiple subscriptions in a single Storage account (in alignment with Microsoft's best practices for centralized logging). The blobs are created by Azure hourly in separate folders. Lacework leverages an Event Grid subscription that creates Queue messages and Lacework pulls the new logs as soon as they appear.
Lacework aggregates and organizes this activity log data into useful maps and dashboards that illustrate the following:
- conceptual relationships
- causes and effects
- interactions between Azure entities
Lacework also automatically generates alerts whenever an activity log event represents a security risk.
Requirements
- Ensure that you are deploying the integration to a supported Azure region.
Create an Azure AD App
To create an Azure AD app, follow the procedure provided in Create an Azure App for Integration. You can skip this procedure if you have already created an Azure app for an Azure compliance integration and reuse the credentials (Gather the Required Azure Client ID, Tenant ID, and Client Secret). This article will refer to the Azure app as LW_ACTLOGREAD_APP_ID.
Register the Necessary Resource Providers
In most cases, if you are already using Azure, this step won't be needed. However, new subscriptions may need to register the necessary Azure Resource Providers. In order to have Activity Logs ingested in Azure, Lacework exports them using Diagnostic Settings (from Azure Monitor) as blobs to a Storage Account with an Event Grid notification to a Queue in the same Storage Account.
Log in to the Azure portal.
In the main search field, enter subscription and select Subscriptions from the drop-down.
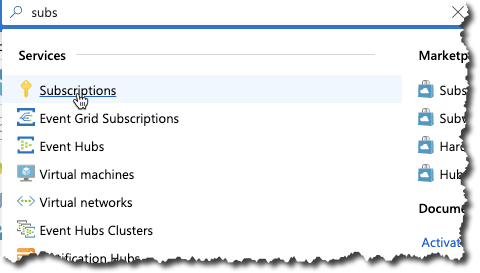
Click your subscription.
Under your subscription, click Settings > Resource providers.
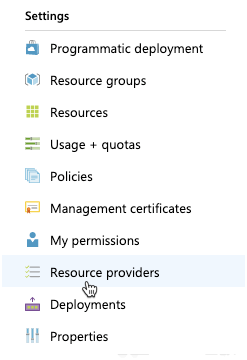
In the filter by name… field, enter Microsoft.Insight.
If the STATUS is NotRegistered, select microsoft.insights and click Register.
Wait until the status changes to Registered. You may need to click Refresh.
In the filter by name… field, enter Microsoft.EventGrid.
If the STATUS is NotRegistered, select Microsoft.EventGrid and click Register.
Wait until the status changes to Registered. You may need to click Refresh.
In the filter by name… field, enter Microsoft.Security.
If the STATUS is NotRegistered, select Microsoft.Security and click Register.
Wait until the status changes to Registered. You may need to click Refresh.
Configure Azure for Activity Log Integration
Open an Azure Cloud Bash shell from the Azure Portal or install and open an Azure CLI window in a terminal window using the az login command. Keep the bash shell or CLI window open.
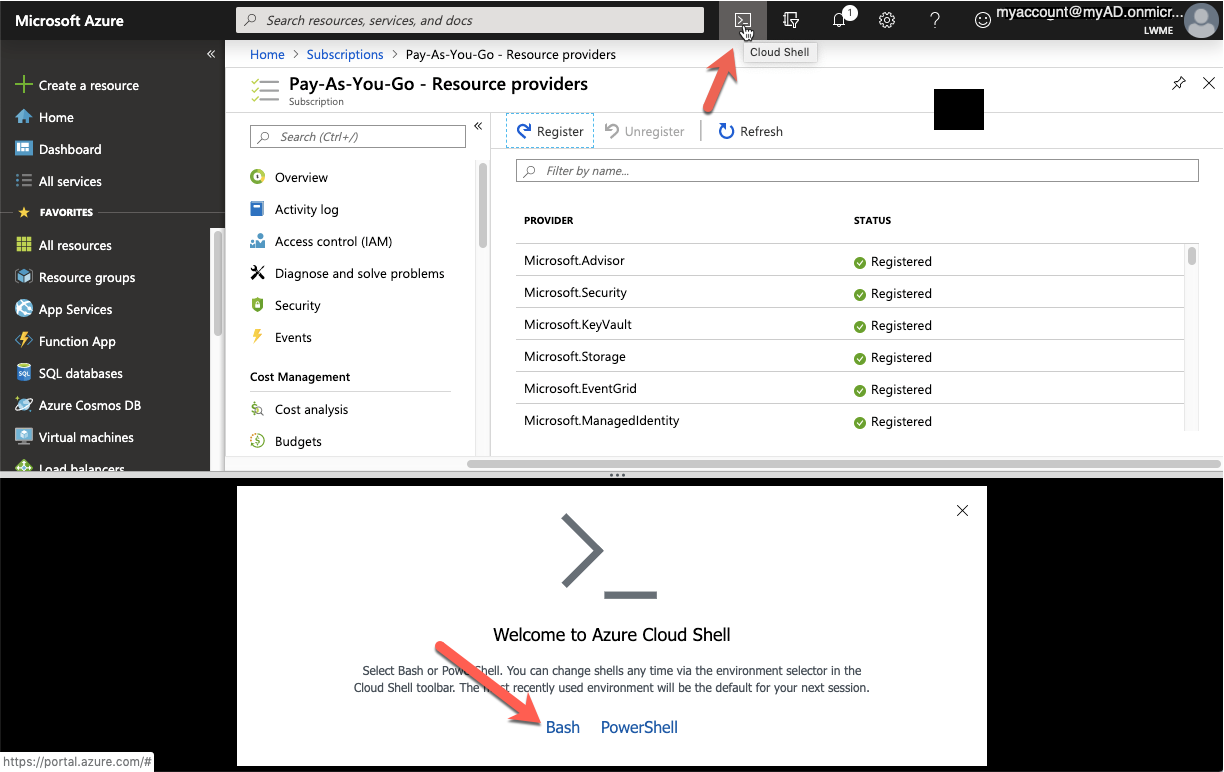
Get the Application ID as described before (Gather the Required Azure Client ID, Tenant ID, and Client Secret). It is referred to as LW_ACTLOGREAD_APP_ID in this article.
In the Azure Cloud Bash Shell, enter appID= and paste the Application (client) ID number and select the return key.
appID=PasteTextHere
echo $appIDUse either an existing storage account that is configured to archive the Azure Activity Log or create a new one. Azure recommends creating a centralized storage account for accessing the Azure Activity Log data.
noteSkip steps 5-6 if you want to use an existing storage account that is configured to archive the Azure Activity Log, and continue at step 7 for EventGrid and the Queue.
To create a new storage account, decide which subscription you want to use to hold the storage account used for activity logging. To change your Azure CLI's active subscription, enter the following:
```
az account list --output table --all
az account set --subscription MySubscriptionName
```In your chosen central logging subscription, create a resource group. Replace westus2 with your location. You can see a list of locations using the
az account list-locationscommand. Enter the location name as listed in the account list-locations command output. You can specify any resource group name.resourcegroup='lacework-collected-logs-rg'
location='westus2'
az group create --location $location --name $resourcegroupCreate a new storage account. For the resource group, specify the resource name you created in the previous step. You can specify any account name, but it cannot be laceworksa123 and it must be a globally unique name. Using $RANDOM adds a 5-digit random number in the shell script below:
storageaccname=laceworksa$RANDOM
az storage account create --name $storageaccname --resource-group $resourcegroup --https-only true --sku Standard_LRS --kind StorageV2Get the Storage Account ID.
storageAccountID=$(az storage account show --name $storageaccname --resource-group $resourcegroup --query id --output tsv)Create an Azure queue to hold notifications about new activity log data.
az storage queue create --name lacework-ingestion-queue --account-name $storageaccnameUse the ID of the queue created in the previous step to create an event grid subscription that will automatically put notifications when new activity log data appears.
queueId="$storageAccountID/queueservices/default/queues/lacework-ingestion-queue"
az eventgrid event-subscription create --name lacework-ingestion-eventgrid --endpoint-type storagequeue --endpoint $queueId --source-resource-id $storageAccountID --subject-begins-with /blobServices/default/containers/insights-activity-logs/ --included-event-types Microsoft.Storage.BlobCreatedCreate and assign a least-privileged Custom Role to the Azure AD application created during setup, so it can only access the resource group containing the storage account with the log blobs and queue messages. You must be an Owner or User Access Administrator in the subscription with the centralized logging storage account.
appID=LW_ACTLOGREAD_APP_ID
resourceGroupID=$(az group show -n lacework-collected-logs-rg --query id --output tsv)
cat << EOF > roleDefinition.json
{
"Name": "Lacework-AuditLog-Reader-Role",
"IsCustom": true,
"Description": "Monitors Activity Log",
"Actions": [
"Microsoft.Resources/subscriptions/resourceGroups/read",
"Microsoft.Storage/storageAccounts/read",
"Microsoft.Storage/storageAccounts/blobServices/containers/read",
"Microsoft.Storage/storageAccounts/queueServices/queues/read",
"Microsoft.EventGrid/eventSubscriptions/read",
"Microsoft.Storage/storageAccounts/listkeys/action"
],
"DataActions": [
"Microsoft.Storage/storageAccounts/blobServices/containers/blobs/read",
"Microsoft.Storage/storageAccounts/queueServices/queues/messages/read",
"Microsoft.Storage/storageAccounts/queueServices/queues/messages/delete"
],
"AssignableScopes": [
"$resourceGroupID"
]
}
EOF
roleDefinition=$(cat roleDefinition.json)
az role definition create --role-definition "$roleDefinition"
az role assignment create --assignee $appID --role Lacework-AuditLog-Reader-Role --scope "$resourceGroupID"Create a Diagnostic Settings config to send Activity Logs to your centralized storage account (Azure only supports the configuration of Diagnostic Settings to subscriptions using the Portal or an ARM template, not the CLI). You can specify any name for the setting, the one used in the following instructions is lacework-activity-logs. We only enable logging for categories Lacework is going to process.
subscriptionID=$(az account show --query id --output tsv)
cat << EOF > lwactivitylog.json
{
"\$schema": "https://schema.management.azure.com/schemas/2018-05-01/subscriptionDeploymentTemplate.json#",
"contentVersion": "1.0.0.0",
"parameters": {
"settingName": {
"type": "string"
},
"storageAccountID": {
"type": "string"
}
},
"resources": [
{
"type": "Microsoft.Insights/diagnosticSettings",
"apiVersion": "2017-05-01-preview",
"name": "[parameters('settingName')]",
"properties": {
"storageAccountId": "[parameters('storageAccountID')]",
"logs": [
{
"category": "Administrative",
"enabled": true
},
{
"category": "Security",
"enabled": true
},
{
"category": "ServiceHealth",
"enabled": false
},
{
"category": "Alert",
"enabled": true
},
{
"category": "Recommendation",
"enabled": false
},
{
"category": "Policy",
"enabled": true
},
{
"category": "Autoscale",
"enabled": false
},
{
"category": "ResourceHealth",
"enabled": true
}
]
}
}
]
}
EOF
az deployment sub create --location $location --template-file lwactivitylog.json --parameters "{\"settingName\":{\"value\":\"lacework-activity-logs\"},\"storageAccountID\":{\"value\":\"$storageAccountID\"}}"(Optional) As explained in step 4, to aggregate audit logs from many other subscriptions in a single centralized storage account, repeat step 11 for each subscription you have in your Azure CLI. First run "az account set --subscription \<name>" and use the same Storage Account ID (referred to in the following example as $centralizedstorageAccountID) for each subscription's log-profile.
az account list --all
## for each other subscription, repeat the commands below, same as step 11, centralizing logs in $storageAccountID ##
az account set --subscription OtherSubscriptionName
subscriptionID=$(az account show --query id --output tsv)
az deployment sub create --location $location --template-file lwactivitylog.json --parameters "{\"settingName\":{\"value\":\"lacework-activity-logs\"},\"storageAccountID\":{\"value\":\"$storageAccountID\"}}"
Alternatively, you could have multiple dedicated Lacework integrations for decentralized Activity Logs (each subscription using its own storage account). In that case, repeat the previous steps for each subscription and:
- Switch the Azure CLI to a different subscription.
- Create the resource group and storage account.
- Create the Event Grid subscription and the Queue.
- Define a Diagnostic Setting to export Activity Logs to that storage account.
- Write down the Storage Account URL and Application Credentials and configure a new integration in the Lacework portal.
Gather the Required Azure Client ID, Tenant ID, and Client Secret
Follow the procedure provided in Gather the Required Azure Client ID, Tenant ID, and Client Secret.
Navigate to Manual Integration
- Log in to the Lacework Console.
- Go to Settings > Integrations > Cloud accounts.
- Click + Add New.
- Click Microsoft Azure and select Manual configuration.
- Click Next.
- Select Activity Log and follow the steps in Create an Azure Activity Log Integration.
Create an Azure Activity Log Integration
- Manually create an Azure application for integration.
- Register the necessary resource providers.
- Configure Azure for Activity Log integration.
- Gather the required Azure details for your integration.
- In the Name field, enter a unique name for the Lacework Console.
- In the Client ID field, enter your Azure client (application) identifier or alias.
- In the Client Secret field, enter the secret key value for your client ID.
- In the Tenant ID field, enter the tenant (directory) identifier.
- In the Queue URL field, enter the queue URL. Go to Storage Accounts, find the Lacework storage account and go to the Queue section to obtain the Queue URL.
- Click Save to finish the Azure integration and save your onboarding progress. The integration appears in the list of cloud accounts under Cloud accounts.
For the “Integration Pending” status, you can hover over the status text and click the refresh icon to fetch the status result again. This does not retest the integration.
Alternative Permissions to Avoid CustomRoles
In order to define a CustomRole, the person executing these instructions must be an Owner or User Administrator for the subscription (for more information, see Azure's custom roles documentation). You may prefer using Built-in roles because it avoids keeping an inventory of the CustomRoles in your environment.
For reference, these are the minimum set of requirements for Lacework's Activity Logs to work properly:
{
"Name": "LaceworkCWS",
"IsCustom": true,
"Description": "Monitors Activity Log",
"Actions": [
"Microsoft.Resources/subscriptions/resourceGroups/read",
"Microsoft.Storage/storageAccounts/read",
"Microsoft.Storage/storageAccounts/blobServices/containers/read",
"Microsoft.Storage/storageAccounts/queueServices/queues/read",
"Microsoft.EventGrid/eventSubscriptions/read",
"Microsoft.Storage/storageAccounts/listkeys/action"
],
"DataActions": [
"Microsoft.Storage/storageAccounts/blobServices/containers/blobs/read",
"Microsoft.Storage/storageAccounts/queueServices/queues/messages/read",
"Microsoft.Storage/storageAccounts/queueServices/queues/messages/delete"
],
"AssignableScopes": [
"/subscriptions/%subscriptionId%/resourceGroups/%resourcegroup%"
]
}
The built-in roles that include these permissions are:
- Storage Account Contributor
- EventGrid EventSubscription Reader
- Storage Blob Data Reader
- Storage Queue Data Contributor
To use them instead of our custom role, replace your step 10 with the following commands:
appID=<LW_ACTLOGREAD_APP_ID>
subscriptionID=$(az account show --query id --output tsv)
# Assign Storage Account Contributor
az role assignment create --assignee $appID --role "17d1049b-9a84-46fb-8f53-869881c3d3ab" --scope "/subscriptions/$subscriptionID/resourceGroups/$resourcegroup"
# Assign EventGrid EventSubscription Reader
az role assignment create --assignee $appID --role "2414bbcf-6497-4faf-8c65-045460748405" --scope "/subscriptions/$subscriptionID/resourceGroups/$resourcegroup"
# Assign Storage Blob Data Reader
az role assignment create --assignee $appID --role "2a2b9908-6ea1-4ae2-8e65-a410df84e7d1" --scope "/subscriptions/$subscriptionID/resourceGroups/$resourcegroup"
# Assign Storage Queue Data Contributor
az role assignment create --assignee $appID --role "974c5e8b-45b9-4653-ba55-5f855dd0fb88" --scope "/subscriptions/$subscriptionID/resourceGroups/$resourcegroup"