Create an Azure App for Integration
The following procedure describes the common manual steps to create an Azure app for use in either an Azure Configuration (Compliance) integration or Azure Activity Log integration. For instructions on creating the entire integration, see the topics in Azure Terraform or Azure Portal.
To manually create an integration using the Azure Portal and the Lacework Console, you must have access to the following:
- An Azure AD account that has a Global Administrator directory role for your tenant (or equivalent administrator rights to create app registrations).
- Your account must have the Owner permissions role in all Azure subscriptions that you want to monitor.
- A Lacework account with administrator privileges.
Overview
This integration procedure describes how to:
- Create a new app registration (named Lacework SA Audit).
- (Optional) Grant it Azure Active Directory permissions (Directory Reader role in Azure AD) to read information from your directory.
- Grant it Azure permissions to read resource configurations from your subscriptions.
- Assign Azure Key Vault permissions if creating an Azure Configuration (Compliance) integration.
About Azure AD Permissions
If choosing to grant permissions to the directory through the Directory Reader role, Lacework will collect the list of users, groups, members, and app registrations from the Azure AD organization using Microsoft Graph API calls. This information is exposed for LQL datasources and compliance policies.
Disabling this permission may be required if your organization has specific regulatory or privacy requirements that do not allow this information to be collected by third parties. If disabled, LQL datasources and related IAM compliance policies will not be assessed.
For existing integrations, at any time, you can remove the Directory Reader role from the Azure AD service principal used for Lacework (created in the following section).
1. Create an Azure App Registration
Log in to the Azure Portal.
In the left panel, select Azure Active Directory.
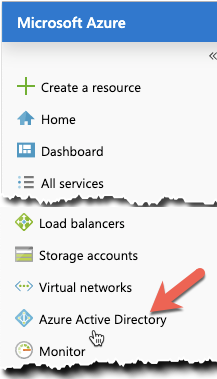
Select App registrations.
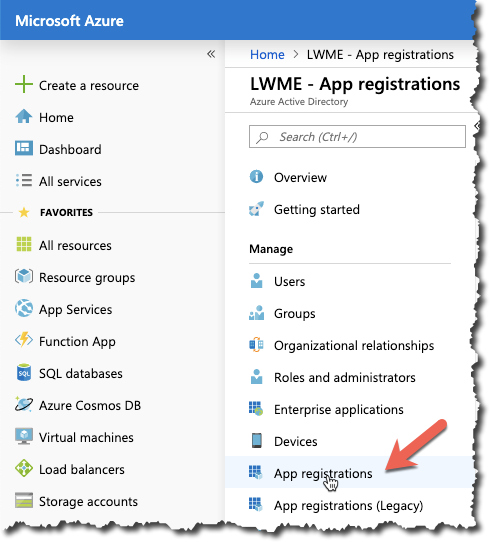
Click + New registration.
In the Register an application panel, enter the following values:
- Name - Enter Lacework SA Audit.
- Supported account types - Leave the default Accounts in this organizational directory only (my_dir) option.
- Redirect URL - Leave the URL blank.
Click Register.
2. Grant the Azure App the Directory Reader Role
This section is optional, see About Azure AD Permissions for more information.
The Azure app you created in the previous section must be given basic permissions to read users information from your directory.
Standard Azure AD Steps
To grant the necessary permissions:
Navigate to Azure Active Directory.
Click Roles and administrators.
Click Directory Reader (click the name, do not select it).
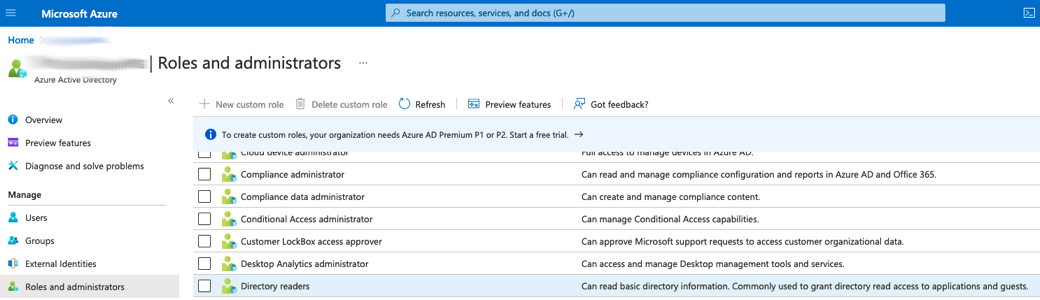
Click Add assignments.
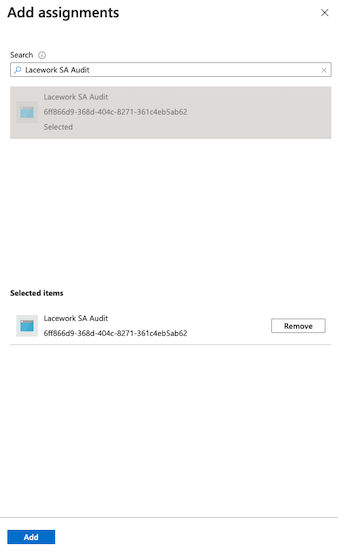
Go to the Add assignments menu, then search for your app registration name, such as Lacework SA Audit, then click Add.
Privileged Identity Management Steps
If you are using Privileged Identity Management, the flow is slightly different:
Navigate to Azure Active Directory.
Click Roles and administrators.
Click Directory Reader (click the name, do not select it).
Click Add assignments.
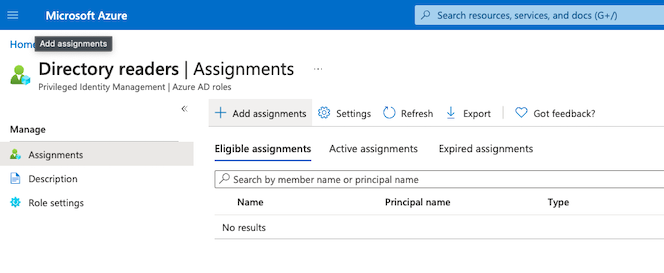
Under Select member(s), click No member selected, then search for your app registration name, such as Lacework SA Audit, then click Select.
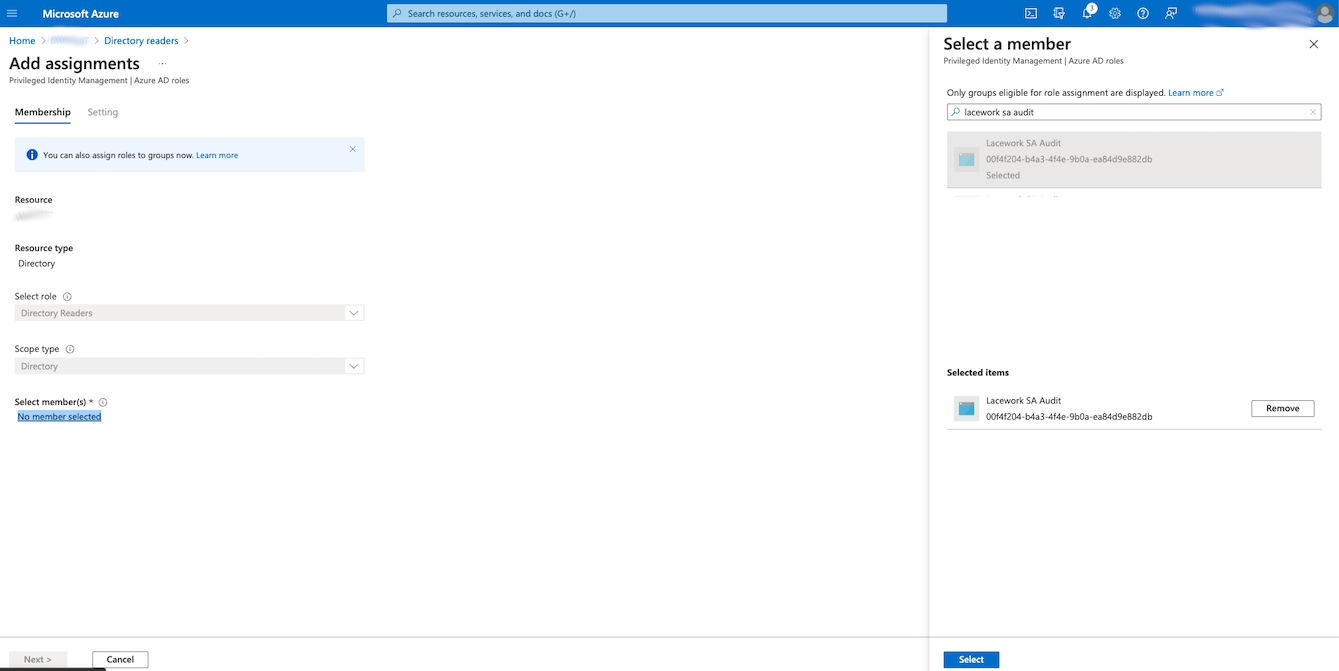
Confirm Membership by clicking Next >.
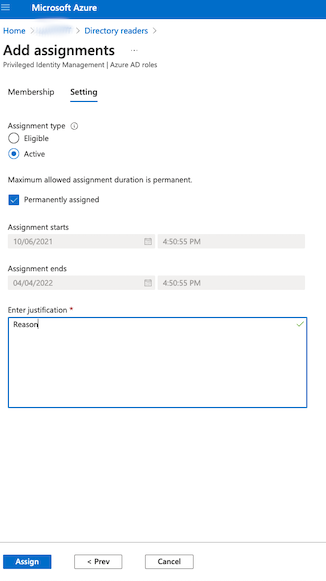
Confirm Setting with assignment type Active, select the Permanently assigned checkbox, and enter a justification. Azure will notify other Azure AD admins about this assignment via email.
3. Assign Reader Permissions to Subscriptions
You must give the Azure App (created for Lacework) Reader permissions to access subscriptions that you want to monitor for proper configuration and compliance. For future CIS compliance checks, extra permissions may be needed.
For more information, see the detailed RBAC description of each role in Azure built-in roles documentation page.
Assign Permissions to a Single Subscription
In the main search field, enter subscription and select Subscriptions from the drop-down.
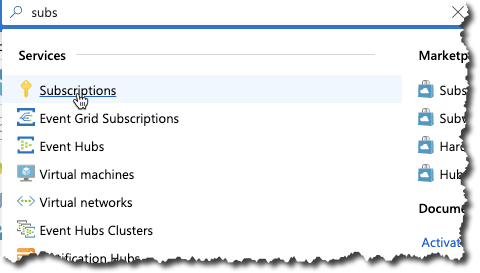
Browse and click your subscription.
Click Access control (IAM).
In the Add a role assignment tile, click Add.
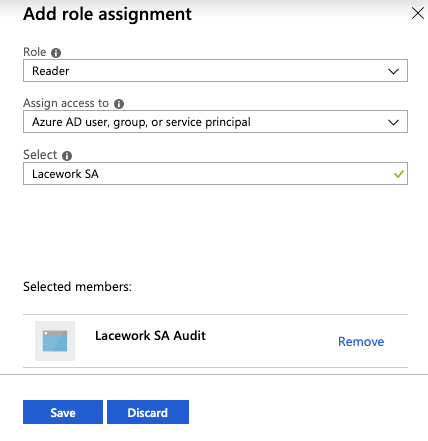
In the Role field, enter Reader.
Leave the Assign access to field set to Azure AD user, group, or service principal.
In the Select field, enter the app name such as Lacework SA.
In the Selected members field, click Lacework SA Audit.
Assign Permissions to All Subscriptions
Repeat the previous steps for all the subscriptions in your tenant. Lacework will automatically detect all visible subscriptions with a single configuration integration.
Optionally, you can assign permissions to a Management Group. Lacework will discover every subscription where the Reader permission has been inherited. This allows organizations with dozens of subscriptions to avoid the manual process of assigning permissions. For more information, visit Azure documentation.
4. Assign Azure Key Vault permissions
This step is only required for Azure Configuration (Compliance) integrations.
Azure Key Vault permissions are required to be able to assess some compliance policies in your environment. Not having the appropriate permissions can result in "Could Not Assess" errors on enabled policies that require Key Vault access.
Grant Azure Key Vault by using one of the following methods:
- Vault access policy (default)
- Azure role-based access control (recommended)
- This method is only available if you have enabled the Azure RBAC access model.
- This method is recommended as any new key vaults added to your subscription or tenant will automatically be accesible for compliance monitoring.
This grants Lacework access to read the necessary metadata required for the compliance policy assessments. This will not grant Lacework access to read the contents of Keys or Secrets (as this is not required).
Option 1: Vault access policy (default)
Key Vault access policies must be added for all existing Key Vaults and any new ones created in the future that you want to monitor.
Follow the steps in Assign a Key Vault access policy and assign the following permissions to the Lacework application (created for the Azure integration):
- Key permissions: List
- Secret permissions: List
Option 2: Azure role-based access control (recommended)
Assign the KeyVaultReader role to the Lacework application (created for the Azure integration) for the subscription or all subscriptions that you are integrating (or have integrated) with Lacework.
If you wish to use this role, Azure RBAC must be enabled.
By using this method, any new key vaults added to your subscription or tenant will automatically be accesible for compliance monitoring.