Configure Access to Labels in Google Cloud
Google Cloud supports user-defined labels to organize your Google Cloud resources. For more information, see Creating and Managing Labels.
The Lacework agent can retrieve the labels from the GCE instances on which the agent is installed and display them in the Lacework Console. This enables you to do the following:
- Use the label values to identify Google Cloud resources displayed in the Lacework Console.
- Use the labels to filter information displayed in the Lacework Console. For example, you can use the Machine tags filter in the Host Vulnerabilities page to view only the vulnerabilities on hosts in a specific Google Cloud project.
Requirements
For the Lacework agent to be able to retrieve user-defined labels on Google Compute Engine (GCE) instances, the service account associated with the instance must have sufficient authorization to retrieve this information over the Compute Engine API. In particular, the instance and its associated service account must possess:
- Read access to the GCE API
- compute.instances.get IAM permission
Configure Access to the Google Compute Engine API
The GCE instance requires the compute.readonly OAuth scope, but broader scopes, such as compute and cloud-platform, also fulfill this minimum level of permission. The default GCE instance policy does not usually contain this scope. So, you need to configure this level of permission to allow Lacework to access the GCE API.
In the Google Cloud Console, click Compute Engine, select the VM Instances page, and then select your instance.
Stop your instance.
On your instance’s page, click Show Details under API and identity management.
See if the menu item for the Compute Engine API is set to either Read Only or Read Write (corresponding to the compute.readonly and compute OAuth scopes, respectively). Alternatively, see if the Cloud API access scopes is set to Allow Full Access (corresponding to the cloud-platform scope).
If the instance does not have any of the permissions described, click Edit.
Scroll down to find a series of drop-downs that grant access to the various Google Cloud APIs and locate the Compute Engine API dropdown.
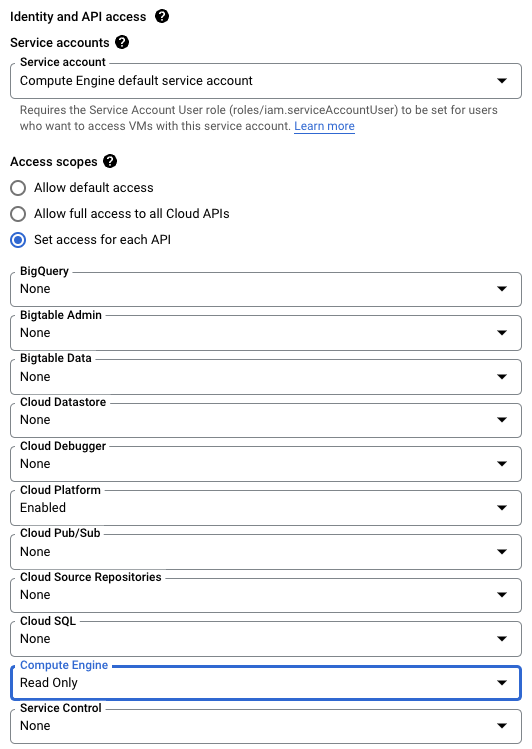
Select the Read Only option.
Select Save at the bottom of this page.
Restart your instance.
Validate Permissions for your Service Account
Most service accounts will be configured with the predefined Editor role and will have enough permissions to allow Lacework to access GCE, requiring no further action on your part. However, if your organization configures GCE service accounts differently, then your service account may not have enough permission. In this case, you or your administrator must either:
- Add a new role to the service account that contains this permission: OR
- Add the permission to a role that the service account already has. Note that this option is only available for custom roles.
For information about viewing and setting up roles for your service account, see Manage access to projects, folders, and organizations.