Google Cloud Integration - Guided Configuration
This topic describes how to use guided configuration to integrate Google Cloud Platform (GCP) with Lacework. Guided configuration is a wizard-like interface that takes your inputs and generates a CLI bundle script that downloads and sets up all necessary Lacework CLI and Terraform components to create the Google Cloud integration. You can run the CLI bundle script in Google Cloud Shell or on any host supported by Terraform.
Requirements
- Ensure that you are deploying the integration to a supported Google Cloud region.
- The final step of guided configuration is to run the generated CLI bundle script from either Google Cloud Shell or any Terraform-supported host. Ensure your environment meets the corresponding requirements.
From Google Cloud Cloud Shell
Google Cloud Shell inherits the permissions of the user running Cloud Shell. Before beginning, determine whether the integration between Google Cloud and Lacework will be at the organization level or the project level, and then ensure the user account running Google Cloud Shell has the following permissions:
- Organization Level Integrations
roles/owner- For an organization level integration, Lacework recommends that you create a new project specifically for the Lacework resources. The user account used to run Google Cloud Shell must haveOwnerpermissions for that project.roles/resourcemanager.organizationAdminroles/iam.organizationRoleAdminroles/logging.configWriter
- Project Level Integrations
roles/owner- For a project level integration, Lacework recommends that you use the project being integrated to provision the required resources. The user account used to run Google Cloud Shell must haveOwnerpermissions for every project being integrated into Lacework.
From Any Terraform-Supported Host
- Google Cloud Console - Administrator access to Google Cloud Console to create projects, service accounts, grant access, and provision resources.
- Google Cloud CLI - To configure resources in Google Cloud. Ensure that you have project owner (for project level integration) or organization administrator (for organization level integration) access on Google Cloud.
- Linux Tools - The following Linux tools must be installed and present on PATH: curl, Git, and unzip.
- Lacework Administrator - A Lacework account with administrator privileges.
Navigate to Guided Configuration
Follow these steps to integrate using guided configuration.
- Log in to the Lacework Console.
- Go to Settings > Integrations > Cloud accounts.
- Click + Add New.
- Click Google Cloud Platform and select Guided configuration.
- Click Next.
- Select an integration type and follow the steps for the corresponding integration type.
- Click Generate CLI Bundle to generate a CLI bundle based on the information entered. You can copy and paste the script to run the CLI bundle into Google Cloud Shell or in a terminal on any Terraform-supported host to create the integration. For more information, see Generate CLI Bundle.
Create an Audit Log (PubSub)+Configuration Integration
If you want to migrate an existing Storage-based audit log integration to a Pub/Sub-based audit log integration, see the following topics:
- Log in to the Lacework Console.
- Go to Settings > Integrations > Cloud Accounts.
- Select the row for the Storage-based audit log integration you set up for the organization. A Storage-based audit log integration has the provider as
GCPand type asAudit Log (Storage)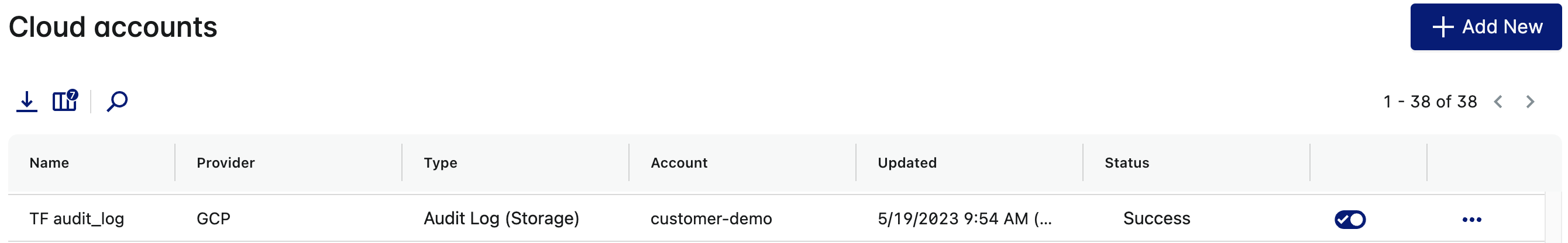 The Cloud Account page displays the integration details.
The Cloud Account page displays the integration details. - Click the Delete icon
to delete the integration.
Basic configuration
Answer the questions about how to configure the integration.
- Do you want to enable GCP Configuration integration?
A Configuration integration analyzes your Google Cloud environment's configuration compliance and reports alerts for anomalous behavior. - Do you want to enable GCP Audit Log (PubSub) integration?
An Audit Log integration analyzes audit log activity and reports alerts for anomalous behavior. - What is the project ID to provision Lacework resources? - Specify the ID of the project to use to provision Lacework resources. Ensure that you have enabled billing for the project.
- Enable organization level integration? - Select to configure an integration at the organization level.
What is the GCP organization ID? - Specify the ID of the organization to integrate. To obtain the organization ID, use the Google Cloud Shellgcloud projects get-ancestors projectIdcommand. - Select an API key.
- Select an existing Lacework API key from the list.
- If no API keys exist, click Create New Key, enter a name and description, and click Save. Then select the key to use in the integration.
Advanced Configuration
For optional advanced configuration, click Advanced configuration (optional) and click Configure for the options you want to configure. The following options are available.
Configuration integration name
- Configuration integration name - A unique name for the configuration integration.
Audit Log integration name
- Audit Log integration name - A unique name for the audit log integration.
Configure Lacework integration with an existing service account
Service account name - Name of the existing service account to use in the integration.
Private key (base64 encoded) - Provide the private key for the service account. To obtain the private key, do the following:
Install the
jqutility from https://stedolan.github.io/jq/.Open a terminal window and go the directory where you downloaded the JSON file containing the service account key.
Enter the following command, where YourFileName.json is the name of the JSON file.
cat YourFileName.json | jq -r '.private_key'Copy all the text displayed in the output including the BEGIN and END lines.
-----BEGIN PRIVATE KEY-----
YourKeyInfo
-----END PRIVATE KEY-----Paste the text into the Private key (base64 encoded) field in the Lacework Console.
Configure log sink options
- Existing log sink name - Name of the existing log sink to use for the integration.
Create an Audit Log (Storage)+Configuration Integration
Starting from September 25, 2023, you cannot create a new Storage-based audit log integration. Lacework recommends that you do the following:
- Create Pub/Sub-based audit log integrations going forward.
- Migrate your existing Storage-based audit log integration to a Pub/Sub-based audit log integration. For more information, see the following topics:
Basic configuration
Answer the questions about how to configure the integration.
- Do you want to enable GCP Configuration integration?
A Configuration integration analyzes your Google Cloud environment's configuration compliance and reports alerts for anomalous behavior. - Do you want to enable GCP Audit Log (Storage) integration?
An Audit Log integration analyzes audit log activity and reports alerts for anomalous behavior. - What is the project ID to provision Lacework resources? - Specify the ID of the project to use to provision Lacework resources. Ensure that you have enabled billing for the project.
- Enable organization level integration? - Select to configure an integration at the organization level.
What is the GCP organization ID? - Specify the ID of the organization to integrate. To obtain the organization ID, use the Google Cloud Shellgcloud projects get-ancestors projectIdcommand. - Select an API key.
- Select an existing Lacework API key from the list.
- If no API keys exist, click Create New Key, enter a name and description, and click Save. Then select the key to use in the integration.
Advanced Configuration
For optional advanced configuration, click Advanced configuration (optional) and click Configure for the options you want to configure. The following options are available.
Set Configuration integration name
- Configuration integration name - A unique name for the configuration integration.
Set Audit Log integration name
- Audit Log integration name - A unique name for the audit log integration.
Configure Lacework integration with an existing service account
Service account name - Name of the existing service account to use in the integration.
Private key (base64 encoded) - Provide the private key for the service account. To obtain the private key, do the following:
Install the
jqutility from https://stedolan.github.io/jq/.Open a terminal window and go the directory where you downloaded the JSON file containing the service account key.
Enter the following command, where YourFileName.json is the name of the JSON file.
cat YourFileName.json | jq -r '.private_key'Copy all the text displayed in the output including the BEGIN and END lines.
-----BEGIN PRIVATE KEY-----
YourKeyInfo
-----END PRIVATE KEY-----Paste the text into the Private key (base64 encoded) field in the Lacework Console.
Configure additional bucket options
- Use existing bucket? - Select to use an existing Cloud Storage bucket and enter the name of the bucket.
- Bucket name - Name of the bucket you want to create.
- Bucket region - Region where you want to create the new bucket. Valid values for multi-regions are
EU,US, orASIA. Alternatively, you can set a single region or dual-regions using the naming convention described in the Google Cloud bucket locations documentation. The default region isUS. - Enable force destroy? - Select to enable force destroy.
- Disable uniform bucket level access? - Select to disable uniform bucket-level access on the audit log bucket. Default behavior enables uniform bucket-level access.
- Number of days to keep audit logs - Number of days to keep audit logs in the bucket before deleting. Leave empty to keep indefinitely (default).
Configure log sink options
- Existing log sink name - Name of the existing log sink to use for the integration.
Create a GKE Audit Log Integration
Answer the questions about how to configure the integration.
Basic Configuration
- What is the Project ID to provision Lacework resources?
Specify the ID of the project to use to provision Lacework resources. - Do you want to enable organization level integration?
Select to configure an organization level integration. What is the GCP organization ID?
Specify the ID of the Google Cloud organization. - Select an API key.
- Select an existing API key from the list.
- If no API keys exist, click Create New Key, provide a name and description, and click Save. Then select the key to use in the integration.
Advanced Configuration
For optional advanced configuration, click Advanced configuration (optional) and click Configure for the options you want to configure. The following options are available.
Configure sink options
- Existing sink name - Name of the existing log sink to use for the integration.
Configure Lacework integration with an existing service account
Service account name - Name of the existing service account to use in the integration.
Private Key (base64 encoded) - Provide the private key for the service account. To obtain the private key, do the following:
Install the
jqutility from https://stedolan.github.io/jq/.Open a terminal window and go the directory where you downloaded the JSON file containing the service account key.
Enter the following command, where YourFileName.json is the name of the JSON file.
cat YourFileName.json | jq -r '.private_key'Copy all the text displayed in the output including the BEGIN and END lines.
-----BEGIN PRIVATE KEY-----
YourKeyInfo
-----END PRIVATE KEY-----Paste the text into the Private Key (base64 encoded) field in the Lacework Console.
Generate CLI Bundle
After providing basic configuration information and any desired advanced configuration information, generate the CLI bundle.
- Click Generate CLI bundle. This generates a CLI bundle based on the information entered. You can copy and paste the script to run the CLI bundle into Google Cloud Shell or in a terminal on any Terraform-supported host to create the integration.
- Ensure your environment meets the requirements for run the CLI bundle.
- Click Copy download bundle command to clipboard.
- As either a project owner (for project level integration) or organization administrator (for organization level integration), go to Google Cloud Shell or a terminal on any Terraform-supported host.
- Paste the command and press enter.
This downloads the Lacework CLI, sets up the CLI with your configuration, calls the CLI non-interactively, and applies Terraform to automatically provision the resources required for the integration in Google Cloud. When the command finishes, the new integration appears in the Cloud accounts page after a screen refresh.
Google Apps Script Projects are hidden by default. Contact Lacework Support if you want to enable visibility of these projects.