Pub/Sub-Based Google Cloud Audit Log Integration - Manual Configuration
This topic describes how to manually create a Lacework Google Cloud Pub/Sub-based audit log integration to gather, process, report, and alert on Google Cloud Cloud Audit Log data.
If you want to manually migrate an existing Storage-based audit log integration to a Pub/Sub-based audit log integration, see Migrate from Storage-based to Pub/Sub-Based Google Cloud Audit Log Integration - Manual Configuration.
You must create a separate Google Cloud integration for reporting and alerting on Google Cloud configuration compliance. For more information, see Google Cloud Configuration Integration - Manual Configuration. You can, however, use the same credentials for both integrations.
When a Google Cloud Audit Log integration is created, Lacework uses a Google Cloud Pub/Sub topic to gather the logs of administrative operations from Google Cloud audit logs. Google Cloud captures detailed audit log data and stores that data in audit logs. Lacework aggregates and organizes this audit log data into useful maps and dashboards that illustrate the following. Lacework also automatically generates alerts whenever an audit log event represents a security risk.
- conceptual relationships
- causes and effects
- interactions between Google Cloud entities
Prerequisites
- Decide if you want to monitor the audit logs at the organization, folder, or project level. If you specify the option to include children when creating the sink at the organization or folder level, all the projects in the organization or the folder export the audit logs to the bucket.
- If you are already exporting your audit logs to a Pub/Sub topic, you can reuse that Pub/Sub topic but the project with the Pub/Sub topic must be granted role access as described in the procedure below.
- Google Cloud Console - Administrator access to Google Cloud Console to create projects, service accounts, grant access, and provision resources.
- gcloud CLI - To configure resources in Google Cloud.
- Lacework Console - Org admin or Account admin access to the Lacework Console is required to create API keys and configure integrations with Lacework.
- jq utility
- Ensure that you are deploying the integration to a supported Google Cloud region.
Create a Google Cloud Service Account and Grant Access
Follow the procedure in Create a Google Cloud Service Account and Grant Access. You can skip this step if you have already created a service account and granted role access when creating a new Google Cloud configuration integration. You can also reuse the same service account.
Enable the Required Google Cloud APIs
Enable APIs for the projects you want to integrate using the procedure in Enable the Required Google Cloud APIs.
Configure Google Cloud for Audit Log Integration
This procedure configures the Google Cloud Audit Log integration to ingest audit log data.
Open a terminal window and initialize the gcloud CLI with the following command:
gcloud initLeave the terminal open.
Log in to the Google Cloud Console.
Decide if you want to export audit logs at the organization, folder, or project level. In addition, select an entity to export audit logs from. An entity is either an organization, folder, or project. The entity must be granted access to the service account and must have the role access as described in Create a Google Cloud Service Account and Grant Access. A project can have access because it was directly granted access or because its parent organization was granted access. Billing must also be enabled for any projects that you want to export audit logs from. Note that if you select the option to include children when creating the sink at the organization or folder level, all projects in the organization or the folder export the audit logs to the Pub/Sub topic.
Obtain the ID of the project where the Pub/Sub topic and sink will be created.
- For an organization level integration, Lacework recommends that you create a new project. If you decide to export audit logs at the project level, this is the project that will export its audit logs.
- For a project level integration, obtain the ID of the project being integrated.
In the terminal, set the following variable. Replace my-first-project-654321 with the ID of the project where the Pub/Sub topic and sink will be created.
projectName=my-first-project-654321Set the current project using the following command.
gcloud config set project "$projectName"If the Updated property [core/project] status is not displayed, make sure the quotes are straight double-quotes. Use straight double-quotes for all the variables used in CLI commands in this procedure.
Create a Pub/Sub topic in the project. Replace mytopicname with your topic name.
topicName=mytopicname
gcloud pubsub topics create "$topicName"Set the name of sink. Replace mysink with your sink name.
sinkName=mysinkCreate the sink. Decide if you want to export the audit logs at the organization, folder, or project level and create the sink. If creating the sink at the organization level, add
\ --include-children --organization=myorganizationidto the end of the following command. If creating the sink at the folder level, add\ --include-children --folder=myfolderidto the end of the following command. If you specify the\ --include-childrenoption when creating the sink at the organization or folder level, all the projects in the organization or the folder export audit logs to the Pub/Sub topic.gcloud logging sinks create "$sinkName" "pubsub.googleapis.com/projects/$projectName/topics/$topicName" --log-filter '(protoPayload.@type=type.googleapis.com/google.cloud.audit.AuditLog) AND NOT (protoPayload.serviceName="k8s.io") AND NOT (protoPayload.serviceName="login.googleapis.com") AND NOT (protoPayload.methodName="storage.objects")'Copy the service account returned by the previous command. Copy the text between the single quotes. In the following example, copy
serviceAccount:123567@gcp-sa-logging.iam.gserviceaccount.com.Please remember to grant `serviceAccount:123567@gcp-sa-logging.iam.gserviceaccount.com` the Pub/Sub Publisher role on the topic.The next two steps grant the
roles/pubsub.publisherrole on the Pub/Sub topic.Enter
sinkServiceAccount=, paste the service account name returned by thegcloud logging sinks createcommand, then press Enter.sinkServiceAccount=serviceAccount:123567@gcp-sa-logging.iam.gserviceaccount.comGrant
roles/pubsub.publisherpermissions to the service account returned by thegcloud logging sinks createcommand.gcloud pubsub topics add-iam-policy-binding "$topicName" --member="$sinkServiceAccount" --role=roles/pubsub.publisherCreate the Pub/Sub subscription (queue) for the Pub/Sub topic. Replace mytopicsub with your Pub/Sub subscription name.
topicSubscriptionName=mytopicsub
gcloud pubsub subscriptions create "$topicSubscriptionName" --topic "$topicName" --ack-deadline=300In the terminal, set the following variable. Replace my-service-account with the email ID of service account you created in your project. This is not the service account returned by the
gcloud logging sinks createcommand above.The service account email ID is in the format:
my-service-account@my-project-name.iam.gserviceaccount.com. Note that the stringserviceAccount:must preface the service account email ID.serviceAccount=serviceAccount:my-service-accountGrant the service account you created in your project the subscriber role on the Pub/Sub subscription. If prompted to install a command group, enter y.
gcloud pubsub subscriptions add-iam-policy-binding "projects/$projectName/subscriptions/$topicSubscriptionName" --member="$serviceAccount" --role=roles/pubsub.subscriberEnter the following command to get the Pub/Sub subscription path that is used when creating the integration in the Lacework Console.
echo "projects/$projectName/subscriptions/$topicSubscriptionName"Copy the resulting Pub/Sub subscription path returned by the echo command for use in the next procedure that creates the integration.
If you are setting up new Google audit logging (instead of leveraging existing Google audit logging), Lacework recommends that you set a retention policy with a minimum of 7 days.
Create the Google Cloud Audit Log Integration on the Lacework Console
- Log in to the Lacework Console.
- Go to Settings > Integrations > Cloud accounts.
- Click + Add New.
- Click Google Cloud Platform and select Manual configuration.
- Click Next.
- Select Audit Log (PubSub) as the integration type.
- For Name, enter a unique name for the audit log integration.
- Follow the steps to either upload GCP credentials or enter the credentials manually.
When creating the Google Cloud integration, you can either upload Google Cloud credentials or enter the credentials manually. Finish creating the integration in the Lacework Console by following the steps described in one of the following sections.
Upload GCP Credentials
To upload Google Cloud credentials, follow these steps:
For Upload GCP Credential, click Choose File, navigate to the JSON key file downloaded when you created the Google Cloud service account, then click Open.
This populates the credential fields.For Integration Level, select Organization or Project. Select Organization if integrating at the organization level. Select Project if integrating at the project level.
Do one of the following:
If integrating at the project level, enter the project ID in the Project ID field.
If integrating at the organization level, enter the Google Cloud organization ID in the Organization ID field.
To obtain the organization ID, do the following:
Log in to the Google Cloud console.
Click the project selection drop-down list in the top menu bar.
From the Select from drop-down list, select the organization that contains the projects that you want the integration to monitor.

Go to IAM & admin > Settings and copy the number in the Organization ID field.
For Subscription Name, paste the Pub/Sub subscription path that you copied in an earlier step. The subscription path is in the following format:
projects/$projectName/subscriptions/$topicSubscriptionNameEnter the Pub/Sub topic ID in the Topic ID field. For example, if you created a Pub/Sub topic named
mytopicname, entermytopicname.Click Save to finish the Google Cloud integration and save your onboarding progress. The integration appears in the list of cloud accounts under Cloud accounts.
The integration appears in the list of cloud accounts under Cloud accounts. A Pub/Sub-based integration has the provider as
GCPand type asAudit Log (PubSub). The integration statusSuccessindicates that Lacework is successfully injesting audit log data from Google Cloud.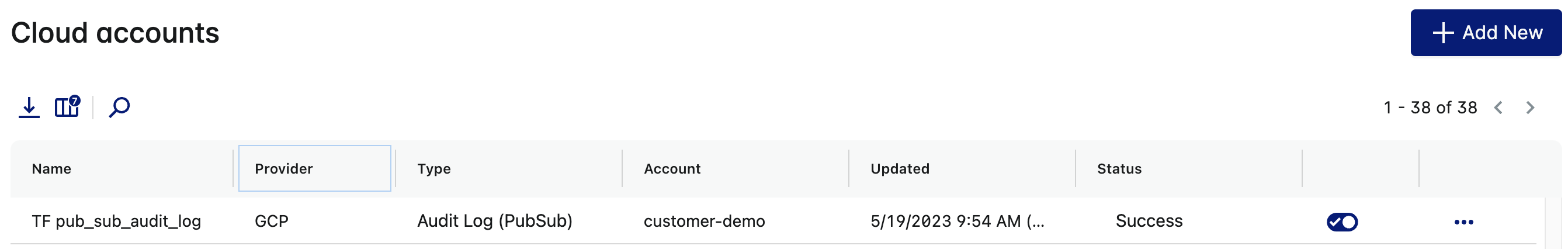
Enter GCP Credentials Manually
To manually enter Google Cloud credentials, follow these steps:
Locate the service account key JSON file you downloaded when you created the Google Cloud service account.
Open the file in a text editor.
Copy the value of the client_id property from the JSON file and paste it into the Client ID field of the Lacework Console.
Copy the value of the private_key_id property from the JSON file and paste it into the Private Key ID field of the Lacework Console.
Copy the value of the client_email property from the JSON file and paste it into the Client Email field of the Lacework Console.
Exit the text editor. You cannot just copy the private key from the editor because of an issue copying the new line characters. You must copy a raw version of the key using the
jqutility as described below.Open a terminal window and go the directory where you downloaded the JSON file containing the service account key.
Verify that the
jq(command-line JSON processor) utility is available from your command-line shell.jqEnter the following command, where YourFileName.json is the name of the service account key JSON file.
cat YourFileName.json | jq -r '.private_key'Copy all the text displayed in the output including the BEGIN and END lines.
-----BEGIN PRIVATE KEY-----
YourKeyInfo
-----END PRIVATE KEY-----Paste the text into the Private Key field of the Lacework Console.
For Integration Level, select Organization or Project. Select Organization if integrating at the organization level. Select Project if integrating at the project level.
Do one of the following:
If integrating at the project level, enter the project ID in the Project ID field.
If integrating at the organization level, enter the organization ID in the Organization ID field.
To obtain the organization ID, do the following:
Log in to the Google Cloud console.
Click the project selection drop-down list in the top menu bar.
From the Select from drop-down list, select the organization that contains the projects that you want the integration to monitor.

Go to IAM & admin > Settings and copy the number in the Organization ID field.
For Subscription Name, paste the Pub/Sub subscription path that you copied in an earlier step. The subscription path is in the following format:
projects/$projectName/subscriptions/$topicSubscriptionNameEnter the Pub/Sub topic ID in the Topic ID field.
Click Save to finish the Google Cloud integration and save your onboarding progress. The integration appears in the list of cloud accounts under Cloud accounts.
The integration appears in the list of cloud accounts under Cloud accounts. A Pub/Sub-based integration has the provider as
GCPand type asAudit Log (PubSub). The integration statusSuccessindicates that Lacework is successfully injesting audit log data from Google Cloud.