GKE Audit Log Integration - Manual
To integrate with GKE, Lacework recommends using Terraform through guided configuration or through the Lacework CLI.
Overview
Lacework integrates with Google Cloud Audit Logs in an event-based streaming pull mode for monitoring GKE admin read, data read, and data write events. This topic describes how to create a GKE integration manually using the Google Cloud Console and the Lacework Console.
Resources
Organization level integrations cover all existing projects in the organization, and automatically add any new projects added after the initial integration.
Project level integrations cover only specific projects and any new projects must be added as required.
To integrate at the organization or project level, Lacework requires the following resources be provisioned in Google Cloud:
- Google Cloud Project - A project to contain the required cloud resources with billing enabled. When integrating at the organization level, Lacework recommends creating a project specifically for Lacework resources. When integrating at the project level, all required resources for Lacework may be provisioned within the project being integrated.
- Google Pub/Sub Topic - Topic for GKE Audit Logs events
- Google Pub/Sub Subscription - Subscription for Lacework to pull the GKE Audit Log events from
- Google Logging Sink - To export Cloud Audit Logs to the Pub/Sub topic
- Service Account for Lacework - To provide Lacework read-only access to Google Cloud Platform with the following roles:
- Organization level integrations
roles/resourcemanager.organizationViewerroles/pubsub.publisherroles/pubsub.subscriberroles/browserroles/monitoring.viewer
- Project level integrations
roles/pubsub.publisherroles/pubsub.subscriberroles/browserroles/monitoring.viewer
- Organization level integrations
For organization level integrations, follow the steps in Integrate GKE Audit Logs at the Organization Level.
For project level integrations, follow the steps in Integrate GKE Audit Logs at the Project Level.
Requirements
Google Cloud Shell - Google Cloud Shell inherits the permissions of the user running Cloud Shell. Before beginning, determine whether the integration between Google Cloud and Lacework will be at the organization level or the project level, and then ensure the user account running Google Cloud Shell has the following permissions:
- Organization level integrations
roles/owner- For an organization level integration, Lacework recommends that you create a new project specifically for the Lacework resources. The user account used to run Google Cloud Shell must haveOwnerpermissions for that project.roles/resourcemanager.organizationAdminroles/iam.organizationRoleAdmin
- Project level integrations
roles/owner- For a project level integration, Lacework recommends that you use the project being integrated to provision the required resources. The user account used to run Google Cloud Shell must haveOwnerpermissions for every project being integrated into Lacework.
- Organization level integrations
Ensure that you are deploying the integration to a supported Google Cloud region.
Google Cloud Shell
Google Cloud Shell is an embedded terminal/command-line interface that you can use within the Google Console. Google Cloud Shell comes with tools pre-installed like the Google Cloud SDK and gcloud command-line tool pre-installed to manage and automate your projects and resources in your environment.
Deployment Scenarios
- Integrate GKE Audit Logs at the Organization Level - This deployment scenario configures a new Lacework GKE Audit Log integration for the entire organization.
- Integrate GKE Audit Logs at the Project Level - This deployment scenario configures a new Lacework GKE Audit Log integration at the single project level.
Integrate GKE Audit Logs at the Organization Level
The following section covers integrating Google Cloud and Lacework for analysis of GKE Audit Logs at the organization level.
Create a Google Cloud Project Using the Google Cloud Console
When creating an integration at the Google Cloud organization level, Lacework recommends having a dedicated project to provision the required resources for the integration between Google Cloud and Lacework.
Create a dedicated project for the integration. Follow the steps in Creating a project.
Configure Project Owner Permissions for User Account
Configure role/owner permission on the project for the user running Google Cloud Shell.
Follow the steps in Grant a single role.
Create a Pub/Sub Topic
Create a Pub/Sub topic. Follow the steps in Create a topic.
Create a Pub/Sub Subscription
Create a subscription for the Pub/Sub topic you just created. Follow the steps in Add a subscription.
Create a Service Account for Lacework
You can reuse the existing service account if you already created one during Google Cloud integration creation.
Create a service account. Follow the procedure in Create a Google Cloud Service Account and Grant Access.
Grant the service account the following roles:
| Role Name | Role ID |
|---|---|
| Pub/Sub Publisher | roles/pubsub.publisher |
| Pub/Sub Subscriber | roles/pubsub.subscriber |
| Organization Viewer | roles/resourcemanager.organizationViewer |
| Browser | roles/browser |
| Monitoring Viewer | roles/monitoring.viewer |
Set up Log Routing
Admin Activity logs are enabled by Google Cloud by default. You can enable Data Access logs at an additional cost from Google Cloud to access the following event groups:
- ADMIN_READ: access to Kubernetes metadata and configuration
- DATA_READ: access to Kubernetes resources
- DATA_WRITE: creation and changes to Kubernetes resources
- In the Google Cloud console, go to IAM & Admin > Audit Logs.
- In the Data Access audit logs configuration table next to Filter, start typing Kubernetes and select Kubernetes Engine API.
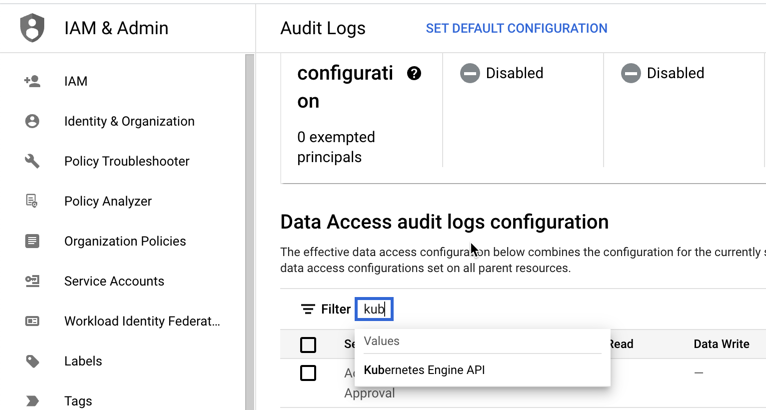
- With Kubernetes Engine API selected, select the logs and click Save.
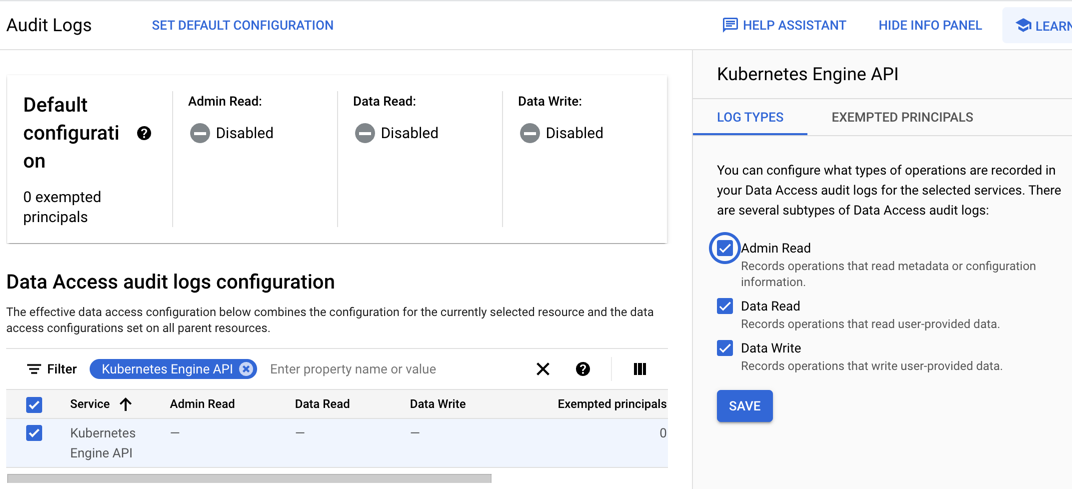
See the following Google Cloud documentation about Configure Data Access audit logs for additional details.
Configure the Log Sink
Configure the Pub/Sub topic as the sink and add inclusion and exclusion filters. Follow the steps in Create a sink.
Add the following inclusion filter:
protoPayload.@type = "type.googleapis.com/google.cloud.audit.AuditLog" AND protoPayload.serviceName = "k8s.io"
Add the following exclusions:
| Name | Filter |
|---|---|
| livezexclusion | protoPayload.resourceName="livez" |
| readyzexclusion | protoPayload.resourceName="readyz" |
| metricsexclusion | protoPayload.resourceName="metrics" |
| clustermetricsexclusion | protoPayload.resourceName="core/v1/namespaces/kube-system/configmaps/clustermetrics" |
Create the GKE Audit Log Integration
- Log in to the Lacework Console.
- Go to Settings > Integrations > Cloud accounts.
- Click + Add New.
- Click Google Cloud Platform and select Manual configuration.
- Click Next.
- Select GKE Audit Log.
- For Name, enter a unique name that displays in the Lacework Console.
- For Client ID, Private Key ID, Client Email, and Private Key, follow these steps:
- Verify that the jq (command-line JSON processor) utility is available from your command-line shell. Leave this command-line window open.
jq - If the jq utility is found, skip to the next step. If the jq utility is not installed or not listed in your PATH, install it (https://stedolan.github.io/jq/) and verify that the path to the utility is listed in your PATH environment variable. The jq utility is required for some steps in the following procedure.
- Locate the JSON key file downloaded when you created the Google Cloud service account.
- Open the file in an editor and leave it open.
- Copy the value of the client_id property from the JSON file and paste the value into the Client ID field of the Lacework Console.
- Copy the value of the private_key_id property from the JSON file and paste the value into the Private Key ID field of the Lacework Console.
- Copy the value of the client_email property from the JSON file and paste the value into the Client Email field of the Lacework Console.
- Exit the editor.
- You cannot just copy the private key from the editor because of an issue copying the new line characters. You must copy a raw version of the key using the “jq” utility as described in the next steps.
- To view the private key raw text, enter the following command, where YourFileName.json is the name of the file downloaded when you created the Google Cloud Service Account.
cat YourFileName.json | jq -r '.private_key' - Copy all text displayed in the output including the BEGIN and END lines.
-----BEGIN PRIVATE KEY-----
YourKeyInfo
-----END PRIVATE KEY----- - Paste the text into the Private Key field of the Lacework Console.
- Verify that the jq (command-line JSON processor) utility is available from your command-line shell. Leave this command-line window open.
- For Integration Level, select Organization.
- For Project ID, copy and paste the project ID.
- For Organization ID, copy and paste the organization ID value. To locate the organization ID:
- Log in to the Google Cloud console.
- Click the down arrow in the top menu bar.
- From the Select from drop-down, select an organization that contains the projects that you want the integration to monitor.
- Select IAM & admin > Settings and copy and paste the number from the Organization ID field.

- For Subscription Name, copy and paste the subscription path. The subscription path is in the following format:
projects/$projectName/subscriptions/$topicSubscriptionName - Click Save to finish the integration. The integration appears in the list of cloud accounts under Cloud accounts.
For the “Integration Pending” status, hover over the status text and click the refresh icon to fetch the status result again. This does not retest the integration.
Integrate GKE Audit Logs at the Project Level
The following section covers integrating Google Cloud and Lacework for analysis of GKE Audit Logs at the project level.
Configure Project Owner Permissions for User Account
Configure role/owner permission on the project for the user running Google Cloud Shell.
Follow the steps in Grant a single role.
Create a Pub/Sub Topic
Create a Pub/Sub topic. Follow the steps in Create a topic.
Create a Pub/Sub Subscription
Create a subscription for the Pub/Sub topic you just created. Follow the steps in Add a subscription.
Create a Service Account for Lacework
You can reuse the existing service account if you already created one during Google Cloud integration creation.
Create a service account. Follow the procedure in Create a Google Cloud Service Account and Grant Access.
Grant the service account the following roles:
| Role Name | Role ID |
|---|---|
| Pub/Sub Publisher | roles/pubsub.publisher |
| Pub/Sub Subscriber | roles/pubsub.subscriber |
| Browser | roles/browser |
| Monitoring Viewer | roles/monitoring.viewer |
Set up Log Routing
Admin Activity logs are enabled by Google Cloud by default. You can enable Data Access logs at an additional cost from Google Cloud to access the following event groups:
- ADMIN_READ: access to Kubernetes metadata and configuration
- DATA_READ: access to Kubernetes resources
- DATA_WRITE: creation and changes to Kubernetes resources
- In the Google Cloud console, go to IAM & Admin > Audit Logs.
- In the Data Access audit logs configuration table next to Filter, start typing Kubernetes and select Kubernetes Engine API.

- With Kubernetes Engine API selected, select the logs and click Save.

See the following Google Cloud documentation about Configure Data Access audit logs for additional details.
Configure the Log Sink
Configure the Pub/Sub topic as the sink and add inclusion and exclusion filters. Follow the steps in Create a sink.
Add the following inclusion filter:
protoPayload.@type = "type.googleapis.com/google.cloud.audit.AuditLog" AND protoPayload.serviceName = "k8s.io"
Add the following exclusions:
| Name | Filter |
|---|---|
| livezexclusion | protoPayload.resourceName="livez" |
| readyzexclusion | protoPayload.resourceName="readyz" |
| metricsexclusion | protoPayload.resourceName="metrics" |
| clustermetricsexclusion | protoPayload.resourceName="core/v1/namespaces/kube-system/configmaps/clustermetrics" |
Create the GKE Audit Log Integration
- Log in to the Lacework Console.
- Go to Settings > Integrations > Cloud accounts.
- Click + Add New.
- Click Google Cloud Platform and select Manual configuration.
- Click Next.
- Select GKE Audit Log.
- For Name, enter a unique name that displays in the Lacework Console.
- For Client ID, Private Key ID, Client Email, and Private Key, follow these steps:
- Verify that the jq (command-line JSON processor) utility is available from your command-line shell. Leave this command-line window open.
jq - If the jq utility is found, skip to the next step. If the jq utility is not installed or not listed in your PATH, install it (https://stedolan.github.io/jq/) and verify that the path to the utility is listed in your PATH environment variable. The jq utility is required for some steps in the following procedure.
- Locate the JSON key file downloaded when you created the Google Cloud service account.
- Open the file in an editor and leave it open.
- Copy the value of the client_id property from the JSON file and paste the value into the Client ID field of the Lacework Console.
- Copy the value of the private_key_id property from the JSON file and paste the value into the Private Key ID field of the Lacework Console.
- Copy the value of the client_email property from the JSON file and paste the value into the Client Email field of the Lacework Console.
- Exit the editor.
- You cannot just copy the private key from the editor because of an issue copying the new line characters. You must copy a raw version of the key using the “jq” utility as described in the next steps.
- To view the private key raw text, enter the following command, where YourFileName.json is the name of the file downloaded when you created the Google Cloud Service Account.
cat YourFileName.json | jq -r '.private_key' - Copy all text displayed in the output including the BEGIN and END lines.
-----BEGIN PRIVATE KEY-----
YourKeyInfo
-----END PRIVATE KEY----- - Paste the text into the Private Key field of the Lacework Console.
- Verify that the jq (command-line JSON processor) utility is available from your command-line shell. Leave this command-line window open.
- For Integration Level, select Project.
- For Project ID, copy and paste the project ID.
- For Subscription Name, paste the subscription path. The subscription path is in the following format:
projects/$projectName/subscriptions/$topicSubscriptionName - Click Save to finish the integration. The integration appears in the list of cloud accounts under Cloud accounts.
For the “Integration Pending” status, hover over the status text and click the refresh icon to fetch the status result again. This does not retest the integration.